This is more of an opinion blog than anything else. However, if I have noticed any trend during all the research I have done for this class, it is one of utter silence from the US Media. I have no fondness for media to begin with, but the complete lack of coverage for cyber attacks, theft, vandalism, and open hostilities is appalling. I would imagine that an attack on our government's nexus of military control would get a little more attention. And of widespread attacks on financial institutions? 30 second blip in the morning news.
Granted, some news agencies do have a section on information security, but I don't believe they are doing enough to make the public aware at just how vulnerable the country's financial and defense data is. I believe that more public knowledge would lead to outrage, not panic, and that congress would be forced to step up funding, and follow Bush's lead to strengthen our data and networks from cyber criminals.
Monday, March 17, 2008
IFRAME Attacks
A week ago, hackers began a scam to redirect people from hundreds of thousands of sites, to malware infected sites. These attacks began one week ago, and continue, expanding at a steady pace. The hackers are utilizing IFRAME injections, and have so far infected 401,000 pages. Experts believe that this is a staging point for a massive, widespread pharming attack. However, the attacks seem to be originating from the Russian Business Network. (source)
This is a perfect example of why Eastern Bloc countries are so dangerous. With most of the worlds malware and illegal sites being hosted in countries that are out of the reach of US and NATO law enforcement organizations, there is little we can do aside from blocking all web traffic that originates in that side of the world, and place a full scale embargo on them to make US credit card and bank numbers far less appealing.
Also, these unified attacks match the description of an act of war to the letter. It weakens our country's infrastructure, endangers the wellbeing of US citizens at home and abroad, and undermines US Military intelligence. I would not be surprised if these actions cause a full scale war in the future.
This is a perfect example of why Eastern Bloc countries are so dangerous. With most of the worlds malware and illegal sites being hosted in countries that are out of the reach of US and NATO law enforcement organizations, there is little we can do aside from blocking all web traffic that originates in that side of the world, and place a full scale embargo on them to make US credit card and bank numbers far less appealing.
Also, these unified attacks match the description of an act of war to the letter. It weakens our country's infrastructure, endangers the wellbeing of US citizens at home and abroad, and undermines US Military intelligence. I would not be surprised if these actions cause a full scale war in the future.
Monday, March 10, 2008
China waging cyber war?
This week, the US Military declared China a "cyber threat" and says they are continuing to wage war in cyberspace using a doctrine of "non-contact warfare." (Source is here). This comes after Germany's accusations in August that the Chinese military sponsored attacks against computers owned by Germany's top officials. In December, the UK's Mi5 warned corporations to be cautious of Chinese attacks.
These recent attacks have convinced the Bush administration to allocate $30 billion towards securing federal networks over the next five to seven years.
The world seems to be getting increasingly suspicious and edgy about China these days, and it is not surprising, considering their recent ability to knock satellites out of orbit. This capability, combined with information garnered from penetration of defense and intelligence networks, would give them unparalleled first strike capabilities.
Armies from developed nations in the west and Europe rely heavily on satellite communications and guidance system for munitions deployment, early detection and warning, and logistical commands. This is compounded by market and financial infrastructure that is entirely reliant on computer systems and networks with national and global communication.
Considering China's move to firewall their entire country and strictly regulate all information into and out of the country, they have much to do if they intend to ease the minds of the rest of the world.
These recent attacks have convinced the Bush administration to allocate $30 billion towards securing federal networks over the next five to seven years.
The world seems to be getting increasingly suspicious and edgy about China these days, and it is not surprising, considering their recent ability to knock satellites out of orbit. This capability, combined with information garnered from penetration of defense and intelligence networks, would give them unparalleled first strike capabilities.
Armies from developed nations in the west and Europe rely heavily on satellite communications and guidance system for munitions deployment, early detection and warning, and logistical commands. This is compounded by market and financial infrastructure that is entirely reliant on computer systems and networks with national and global communication.
Considering China's move to firewall their entire country and strictly regulate all information into and out of the country, they have much to do if they intend to ease the minds of the rest of the world.
Labels:
China,
global,
governments,
intelligence,
satellites,
space,
warfare
crack wifi with the easy button
So I was browsing the backtrack forums, and someone had a link to this little gem:
I should mention that:
A) This is illegal. We're talking 3 years in prison illegal.
B) If you have to download and use that program, you deserve to spend 3 years in jail. And a darwin award.
I should mention that:
A) This is illegal. We're talking 3 years in prison illegal.
B) If you have to download and use that program, you deserve to spend 3 years in jail. And a darwin award.
Sunday, March 9, 2008
Hacking DNA
Oddly enough, the face of Network and Data Security may be changing, and rather grotesquely. Because DNA works in much the same way as machine language, researches have been copying software hackers for methods of reverse engineering genetic code. Probably the most frightening aspect is that virus fabrication costs as little as $20,000 for a complete setup. The code for viruses can be found all over the internet, and run through a DNA synthesizer. Because of the basic nature of a virus, it is the equivalent of a script. It does not need to be compiled, and can even be self executing.
The synthesizer works by printing enzymes for the viral protein onto an organic media, much like a inkjet printer squirts ink onto a sheet of paper. Once the code is completed, the virus actually pulls together into a living organism.
Thanks to advancements in computing technology, and a little hacker know-how, there are high school programs popping up world wide which allow students to do just this.
This video shows a
conference on hacking biology.
I believe that a field of information and data security in the future will include bioinformatics.
The synthesizer works by printing enzymes for the viral protein onto an organic media, much like a inkjet printer squirts ink onto a sheet of paper. Once the code is completed, the virus actually pulls together into a living organism.
Thanks to advancements in computing technology, and a little hacker know-how, there are high school programs popping up world wide which allow students to do just this.
This video shows a
conference on hacking biology.
I believe that a field of information and data security in the future will include bioinformatics.
Saturday, March 1, 2008
joys of patching Vista
I decided to go ahead and dual boot a copy of Windows Vista Ultimate on my computer. First thing that I noticed was the distinct lack of options. You have... format and install. Thats pretty much it. so I installed it on a partition I had already made with windows XP. It more or less installed okay, and there were no serious problems.
So I start to download and install security patches for it. They seem to install okay, but when I restart Vista, it goes something like this:
configuring update 1 of 3... (wait 10 minutes) updates are configured incorrectly, reverting changes. Will attempt again at startup... (wait 10 minutes for changes to revert)... BLUE SCREEN OF DEATH!!! Restart computer manually... cmos errors out... no keyboard present... reboot again... error out again... unplug power supply and wait a few minutes, reconnect and power up... cmos is reset... reconfigure cmos correctly and restart... configuring updates 1 of 3 (wait 10 minutes) updates are configured incorrectly, reverting changes... shutting down... pops into login screen (without shutting down)
So I log in and check the updates. It says they are all installed, so I try to install another round of updates. Programs that require the updates that are "installed" refuse to run, claiming that the updates are not present. Yet the software manager in vista claims they are in the registry.
I spent the next 2 hours trying to get the security updates to pull through and install correctly, but failed every attempt.
Curious.
I do a google for the problem, and find that this is not an isolated incident, but many other people seem to be having trouble getting updates for vista, and it is linked to 2 problems.
1) Vista not running the patch with administrator privileges
2) double byte characters (such as kanji or other foreign languages).
I am going to reinstall Vista Ultimate in case the memory dump during patching corrupted the OS, and try again. I will also try to get some screen shots of it.
Overall, my opinion of the OS is very very low. Out of the ~6 hours I spent with it, 2.5 hours was spent failing to patch, 1 hour was spent recovering from lock ups and crashes, 1 hour was spent digging through drivers and programs to find compatible software (MSN only the latest version of MSN Live Messenger will run on Vista, it isn't pre-loaded, and it crashes on startup so you have to manually restart it), and another 1 hour was spent trying to find fixes for everything that doesn't work. The 1.5 hours I spent trying to learn the OS left me with a bittersweet taste. I feel that most of the changes were unnecessary, and only make the OS more confusing.
I'm assuming that most people will disable the program warning feature, and run as administrator as they do in WinXP, completely defeating the purpose of Vista's only true security improvement over XP.
UPDATE
After reinstalling vista, and adding one driver at a time, I was able to keep the OS stable. The problems have been minimal so far, but I have noticed that downloading and installing updates takes far longer on vista than it does on xp.
So I start to download and install security patches for it. They seem to install okay, but when I restart Vista, it goes something like this:
configuring update 1 of 3... (wait 10 minutes) updates are configured incorrectly, reverting changes. Will attempt again at startup... (wait 10 minutes for changes to revert)... BLUE SCREEN OF DEATH!!! Restart computer manually... cmos errors out... no keyboard present... reboot again... error out again... unplug power supply and wait a few minutes, reconnect and power up... cmos is reset... reconfigure cmos correctly and restart... configuring updates 1 of 3 (wait 10 minutes) updates are configured incorrectly, reverting changes... shutting down... pops into login screen (without shutting down)
So I log in and check the updates. It says they are all installed, so I try to install another round of updates. Programs that require the updates that are "installed" refuse to run, claiming that the updates are not present. Yet the software manager in vista claims they are in the registry.
I spent the next 2 hours trying to get the security updates to pull through and install correctly, but failed every attempt.
Curious.
I do a google for the problem, and find that this is not an isolated incident, but many other people seem to be having trouble getting updates for vista, and it is linked to 2 problems.
1) Vista not running the patch with administrator privileges
2) double byte characters (such as kanji or other foreign languages).
I am going to reinstall Vista Ultimate in case the memory dump during patching corrupted the OS, and try again. I will also try to get some screen shots of it.
Overall, my opinion of the OS is very very low. Out of the ~6 hours I spent with it, 2.5 hours was spent failing to patch, 1 hour was spent recovering from lock ups and crashes, 1 hour was spent digging through drivers and programs to find compatible software (MSN only the latest version of MSN Live Messenger will run on Vista, it isn't pre-loaded, and it crashes on startup so you have to manually restart it), and another 1 hour was spent trying to find fixes for everything that doesn't work. The 1.5 hours I spent trying to learn the OS left me with a bittersweet taste. I feel that most of the changes were unnecessary, and only make the OS more confusing.
I'm assuming that most people will disable the program warning feature, and run as administrator as they do in WinXP, completely defeating the purpose of Vista's only true security improvement over XP.
UPDATE
After reinstalling vista, and adding one driver at a time, I was able to keep the OS stable. The problems have been minimal so far, but I have noticed that downloading and installing updates takes far longer on vista than it does on xp.
Friday, February 29, 2008
Scanning and Jamming Wireless
So, I was kicked back, having a drink or two and enjoying my time away from vista (more on that in another blog) and thinking. For some reason, my mind went to WWII, and America's invention of a radio jamming defense system. It dawned on me that the same technique could be applied in reverse to protect wireless access points.
Current wireless protection depends on encryption standards. While these standards can be rather good, they rely on the premise that the data will be long out dated and useless by the time an attacker could crack the encryption protecting it. Indeed, (theoretically speaking), a 16 character password using upper case, lowercase, special characters (not on the top row) and numbers would take more than one person's life time to break.
However, as computers and processors become more and more powerful, the time required to break encryption dramatically falls to a mere fraction of what it once was. Current computers would take only a few seconds to crack the encryption that enigma machines used in WW2.
So why bother with a jamming procedure which was invented in WW2? Because it is the basic premise that can be replicated and updated to fit our needs today. The machine that I am talking about worked using a device similar to the old rotating drum inside a piano. The device would cycle channels, and only using another key that matched exactly would allow you to change channels in sync with anyone else you needed to communicate with. By the end of the war, the German's could not listen in on American or British communication, and could not jam a broad enough spectrum of channels to prevent communication either. Here is the basic outline:
You have a large corporate campus. AP's are scattered all over it so that employees can use laptops to complete work. Each laptop is set up with special software that syncs with the AP controllers. Every one second (probably less, 250ms would probably be better) the channel changes on the AP's. The laptops change along with the AP's, so the connection is not lost.
Now, this prevents someone from simply pulling ivs (you did read my wep hacking tut, correct?) But it doesn't prevent them from scanning channels, and eventually discovering the pattern.
So you have to use a jammer as well. This operates at the same rate as the AP's, except it jams every channel except for the one in use. This way, their AP should continue to fail to find any transmissions, and should hopefully be instantly disconnected from any connection they may get on accident.
Just a thought, and requires a lot more in depth though and engineering than this blog entry includes.
Current wireless protection depends on encryption standards. While these standards can be rather good, they rely on the premise that the data will be long out dated and useless by the time an attacker could crack the encryption protecting it. Indeed, (theoretically speaking), a 16 character password using upper case, lowercase, special characters (not on the top row) and numbers would take more than one person's life time to break.
However, as computers and processors become more and more powerful, the time required to break encryption dramatically falls to a mere fraction of what it once was. Current computers would take only a few seconds to crack the encryption that enigma machines used in WW2.
So why bother with a jamming procedure which was invented in WW2? Because it is the basic premise that can be replicated and updated to fit our needs today. The machine that I am talking about worked using a device similar to the old rotating drum inside a piano. The device would cycle channels, and only using another key that matched exactly would allow you to change channels in sync with anyone else you needed to communicate with. By the end of the war, the German's could not listen in on American or British communication, and could not jam a broad enough spectrum of channels to prevent communication either. Here is the basic outline:
You have a large corporate campus. AP's are scattered all over it so that employees can use laptops to complete work. Each laptop is set up with special software that syncs with the AP controllers. Every one second (probably less, 250ms would probably be better) the channel changes on the AP's. The laptops change along with the AP's, so the connection is not lost.
Now, this prevents someone from simply pulling ivs (you did read my wep hacking tut, correct?) But it doesn't prevent them from scanning channels, and eventually discovering the pattern.
So you have to use a jammer as well. This operates at the same rate as the AP's, except it jams every channel except for the one in use. This way, their AP should continue to fail to find any transmissions, and should hopefully be instantly disconnected from any connection they may get on accident.
Just a thought, and requires a lot more in depth though and engineering than this blog entry includes.
Thursday, February 28, 2008
Interim Post
This isn't really a full entry, but I thought it was worth a read. This website has a list of security certifications, their cost, difficulty, standing in the IT world, and some commentary on the content of the exam.
Anyone who is interested in Network Security should have a look at it.
Anyone who is interested in Network Security should have a look at it.
Monday, February 25, 2008
Default Security
So, I was browsing the SANS top 20 security risks of 2007 here and noticed they mentioned the weak or complete lack of default passwords, and/or prompting for new passwords. I also ran into this discussion on the backtrack.org forums.
The essential problem is that manufacturers add setup wizards which either skip the subject of passwords and security, or only touch on the default password. Everyone in networking knows that a linksys router has the user name and password of admin, for example.
So why can't manufacturers:
A) Enable high security features by default (IE WPA)?
B) Randomly generate a 16 character password with upper and lower case letters, and numbers?
c) Ask users if they want to enable low security features, such as wireless communication or auto-form completion?
Don't manufacturers have that responsibility? Now, it is understandable that companies like Cisco do not add any programming to their high end equipment, as only certified professionals are expected to purchase and implement the equipment anyway. But an employee with a poorly configured PDA could pose a huge security risk to the company.
That's not to mention bluetooth devices that still have the default code of 0000.
While it's true that the ultimate responsibility is that of the end user, manufacturers should not be promoting products that are easy to use and "easy to install" if they are not equally easy to secure.
The essential problem is that manufacturers add setup wizards which either skip the subject of passwords and security, or only touch on the default password. Everyone in networking knows that a linksys router has the user name and password of admin, for example.
So why can't manufacturers:
A) Enable high security features by default (IE WPA)?
B) Randomly generate a 16 character password with upper and lower case letters, and numbers?
c) Ask users if they want to enable low security features, such as wireless communication or auto-form completion?
Don't manufacturers have that responsibility? Now, it is understandable that companies like Cisco do not add any programming to their high end equipment, as only certified professionals are expected to purchase and implement the equipment anyway. But an employee with a poorly configured PDA could pose a huge security risk to the company.
That's not to mention bluetooth devices that still have the default code of 0000.
While it's true that the ultimate responsibility is that of the end user, manufacturers should not be promoting products that are easy to use and "easy to install" if they are not equally easy to secure.
Thursday, February 21, 2008
Hex Editing
What is hex editing? Hex editing is a method of altering files based on hex instead of using given editing software, such as notepad or visual basic. This is not the quickest method of altering a file, but it will allow you to access portions of files that are otherwise concealed.
So is this a security concern? Absolutely. hex editing can be used on data in system memory as well as data stored on the hard drive.
Here I'm using FlexHEX. You can see that selecting the hex will also show you the plain text translation, and vice versa.


This is how easy it is to edit the text in a text file. You can also alter checksums as such:

Note that I did not alter a file from an actual program, because it is illegal. Tampering with any files from an installed or running program is considered reverse engineering.
So is this a security concern? Absolutely. hex editing can be used on data in system memory as well as data stored on the hard drive.
Here I'm using FlexHEX. You can see that selecting the hex will also show you the plain text translation, and vice versa.


This is how easy it is to edit the text in a text file. You can also alter checksums as such:

Note that I did not alter a file from an actual program, because it is illegal. Tampering with any files from an installed or running program is considered reverse engineering.
Monday, February 18, 2008
Security Videos
For this blog, I'll just link to some interesting security videos.
Hacking Cisco
Cisco Security Training Video (cheesy)
Understanding IPSEC
Hacking Methodologies
Ethical Hacker
And a video from the SANS institute on Security Certification
Hacking Cisco
Cisco Security Training Video (cheesy)
Understanding IPSEC
Hacking Methodologies
Ethical Hacker
And a video from the SANS institute on Security Certification
Friday, February 15, 2008
making a Bart PE setup disk
Making a Bart PE disk is both more and less difficult than making a nLite disk. It is easier because you can make an image immediately, using no additional parameters. However, to actually make a useful disc, there are substantially more steps involved.
I was going to do a tutorial on this, but I do not have the time. Instead, I will add a few highlights.
Diversity
Bart PE is a live install, which means it installs to RAM, but runs like a fully operational OS. Because it also has full network support, it allows you to install an OS to a computer from a remote location. What is the advantage of this? Well, lets say you have two or more domains that clients must be configured for, and multiple brands of workstations. How will you fit all of that on a single CD, which only has enough space for one OS?
The answer is to put multiple images on a server, and add a file browser to Bart PE. Simply choose the image you wish to install from the server and run with it.
Security
nLite is great for convenience, but if anyone ever steals a CD, your CD key and any pre-installed software is now compromised. Simply stealing a Bart PE is but a single step in several more requirements. First, none of the images are stored on the disk, so you must have a password with permissions to access them. If the thief manages to do this, and install an image, they will still need a viable domain logon. If they change the admin password, they have only been able to get a free copy of XP (through a lot of work) but still don't have access to any data.
While this is far from unbreakable (there are several ways around the security) it is still better than no security at all.
Options
You can preload some diagnostic tools, virus scanners, and other useful third party tools. These can be run from the live install, in the even that the computer won't boot. This can greatly simplify the troubleshooting process, saving hours of work and therefore money.
Future Proofing
Because the image is not on the disk, it can be updated, removed, and new images added without any changes to the Bart PE disc. This is a great boon for administrators that do not want to waste time re-creating restore discs.
Drawbacks
Bart PE is not perfect. It requires knowledge of passwords, domain names, and image types. This means installation takes longer and should only be performed by qualified personnel.
Furthermore, because the images are installed over the network, a server must be dedicated for this purpose and enough bandwidth must be reserved. Smaller companies may find this more difficult, and it further increases the amount of time required for an install.
I did find a tutorial that was already created.
I was going to do a tutorial on this, but I do not have the time. Instead, I will add a few highlights.
Diversity
Bart PE is a live install, which means it installs to RAM, but runs like a fully operational OS. Because it also has full network support, it allows you to install an OS to a computer from a remote location. What is the advantage of this? Well, lets say you have two or more domains that clients must be configured for, and multiple brands of workstations. How will you fit all of that on a single CD, which only has enough space for one OS?
The answer is to put multiple images on a server, and add a file browser to Bart PE. Simply choose the image you wish to install from the server and run with it.
Security
nLite is great for convenience, but if anyone ever steals a CD, your CD key and any pre-installed software is now compromised. Simply stealing a Bart PE is but a single step in several more requirements. First, none of the images are stored on the disk, so you must have a password with permissions to access them. If the thief manages to do this, and install an image, they will still need a viable domain logon. If they change the admin password, they have only been able to get a free copy of XP (through a lot of work) but still don't have access to any data.
While this is far from unbreakable (there are several ways around the security) it is still better than no security at all.
Options
You can preload some diagnostic tools, virus scanners, and other useful third party tools. These can be run from the live install, in the even that the computer won't boot. This can greatly simplify the troubleshooting process, saving hours of work and therefore money.
Future Proofing
Because the image is not on the disk, it can be updated, removed, and new images added without any changes to the Bart PE disc. This is a great boon for administrators that do not want to waste time re-creating restore discs.
Drawbacks
Bart PE is not perfect. It requires knowledge of passwords, domain names, and image types. This means installation takes longer and should only be performed by qualified personnel.
Furthermore, because the images are installed over the network, a server must be dedicated for this purpose and enough bandwidth must be reserved. Smaller companies may find this more difficult, and it further increases the amount of time required for an install.
I did find a tutorial that was already created.
Labels:
backup,
Bart PE,
live install,
Restore,
streamline
Wednesday, February 6, 2008
Honeypots
Honeypots are servers set to run in a DMZ with software and data that appears to be genuine company information. By tricking attackers into believing that this fake information is real, it deters them from further probing on the network. But they do more than just this. Some basic information on honey pots can be found at honeypots.net.
So how much further can you go with honey pots? How cost effective and efficient are they?
This article goes into great detail about defeating honeypots and their purpose. This detail becomes extremely technical, so be warned. I will try to do a break down of it further along.
Honeypots are not just a tool used by independent companies to thwart hackers. A project has been created to categorize and record all malicious activity on honeypots world wide. You can find information on this project at the honeynet website. The SANS website also has an entire paper published that goes into detail about honeypots. This can be found on the SANS website.
Now lets look at the potential of a honeypot, past being a simple false positive for attackers. There are two things than a honeypot can be: proactive and reactive.
Proactive honeypots: These honeypots interact with the attackers, disconnecting and banning them from the network, or returning malicious code to their machines. The later is still illegal, and the distribution of damaging code cannot be suppressed once it is released. If the attacker is on a legitimate network, the entire network could be infected and compromised.
It also has the downside of advertising your security system as soon as the attack is reciprocated, allowing the attacker enough information to attempt to bypass that security function when they attempt a second attack.
Reactive honeypots: Despite the name, these are considered "passive" honeypots. Instead of actively fighting back against attackers, these honeypots gather information on their habits, how they react to certain types of information, even their reaction upon discovering that they are in a honeypot. Though these are mainly used to prevent hackers from penetrating further into the network, they can also be used to track the location of the attacker, and block entire ranges of IP addresses.
Both types of honeypots can also attract spam attacks, absorbing what would otherwise be a very annoying stream of unwanted messages.
So how much further can you go with honey pots? How cost effective and efficient are they?
This article goes into great detail about defeating honeypots and their purpose. This detail becomes extremely technical, so be warned. I will try to do a break down of it further along.
Honeypots are not just a tool used by independent companies to thwart hackers. A project has been created to categorize and record all malicious activity on honeypots world wide. You can find information on this project at the honeynet website. The SANS website also has an entire paper published that goes into detail about honeypots. This can be found on the SANS website.
Now lets look at the potential of a honeypot, past being a simple false positive for attackers. There are two things than a honeypot can be: proactive and reactive.
Proactive honeypots: These honeypots interact with the attackers, disconnecting and banning them from the network, or returning malicious code to their machines. The later is still illegal, and the distribution of damaging code cannot be suppressed once it is released. If the attacker is on a legitimate network, the entire network could be infected and compromised.
It also has the downside of advertising your security system as soon as the attack is reciprocated, allowing the attacker enough information to attempt to bypass that security function when they attempt a second attack.
Reactive honeypots: Despite the name, these are considered "passive" honeypots. Instead of actively fighting back against attackers, these honeypots gather information on their habits, how they react to certain types of information, even their reaction upon discovering that they are in a honeypot. Though these are mainly used to prevent hackers from penetrating further into the network, they can also be used to track the location of the attacker, and block entire ranges of IP addresses.
Both types of honeypots can also attract spam attacks, absorbing what would otherwise be a very annoying stream of unwanted messages.
Hacking WPA
DISCLAIMER: Yes, this will show you how to hack into a wireless network. This is very much ILLEGAL. The purpose of this writeup is for educational purposes only. I am demonstrating the weakness of WPA encryption on my own network. If you wish to try this for yourself, I suggest you buy a wireless router and attempt to crack that.
_____________________________________________________________________
Okay, so I'm not going to back track (forgive the pun) through the previous tutorial. If you aren't certain how to get to where I'm beginning this tutorial at, scroll down and read hacking WEP. It will fill you in on everything except putting your card into monitor mode and such.
So, first you will need to start up airodump-ng and capture packets from the AP. This time, however, do not add the --ivs, as you will want ALL the data in the packets. Look in the upper right corner of the window, just after the date and time. You will notice that the area is black and empty. This is where the four-way WPA handshake will show up when you have attained it. I will explain that in more detail later.
I will assume that you are now collecting packets in monitor mode. Packets by themselves are completely useless for cracking WPA. What we are interested in is the four-way handshake. To get this, we will use aireplay-ng to perform a deauth (de-authentication) attack, disconnecting the client from the AP, and forcing it to reconnect... also giving away the four-way handshake.
To do this, type in aireplay-ng -0 1 -a (AP MAC) -c (Client MAC) (your NIC)
Mine was aireplay-ng -0 1 -a 00:40:05:26:B3:C0 -c 00:16:CF:0B:0D:FD eth2
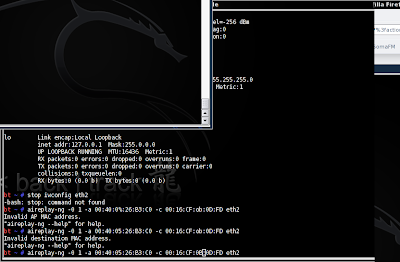
Now you should see a handshake appear in the window containing your running (you did leave it running, right?) airodump-ng program:
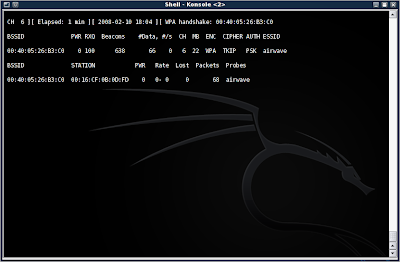
Now we need to get the key. Just as in the WEP cracking tutorial, I am going to make you do some of your own leg work. You will need to find a dictionary word list. You can also make your own, and add the pass phrase to the list. This screenshot shows an example of the list I made in a few seconds to show you the next steps:
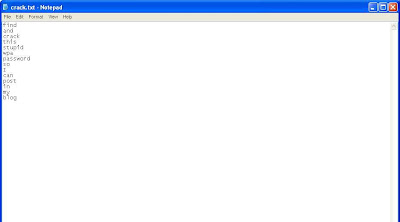
Okay okay, you got me. This was done in Windows XP. I forgot to take a screenshot of the list in BackTrack 3b, and was too lazy to go back and do it again. You'll just have to pretend its all black and fancy and cool looking like the BackTrack GUI is.
Alright, so you have your dictionary list ready to run with aircrack-ng. Type in aircrack-ng -w (dictionary.lst/txt) -b (AP MAC) (dumpfile.cap)
Mine has aircrack-ng -w crack.txt -b 00:40:05:26:B3:C0 psk-02.cap
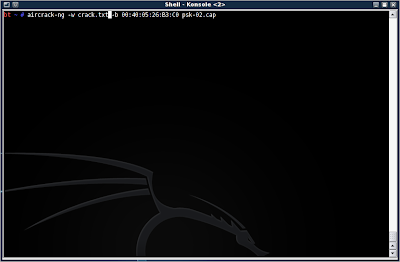
Now, if it finds the correct pass phrase in the dictionary list, you will be presented with the word:
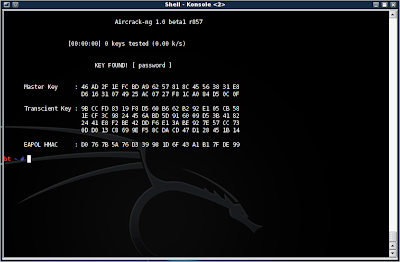
Okay, so what did we learn here? Well, WPA-psk is more secure than WEP in that you must run a dictionary attack against it, and stronger passwords will require a rainbow table (don't worry, I may go into that in another blog). So it is theoretically more secure than WEP.
However, the pass phrase is only as secure as you make it. In this case, I set mine up to be very simple to facilitate this demonstration. However, using real words greatly diminishes the effectiveness of WPA, and it is highly suggested that you use special characters, upper case, lower case, and numbers in your passwords.
The second weakness in WPA-psk, is the reliance on the four-way handshake, in which the key is transmitted. It takes only a moment to run a deauth attack to force a handshake and grab the key.
Finally, WPA has the advantage of requiring a client to be connected before an attempt to crack can occur. Where WEP can be coaxed into transmitting packets, and therefore give the attacker IVs, WPA cracking needs that handshake with the pass phrase before any further progress can be made.
So WPA is far from perfect, but it can foil someone who is unprepared to run a dictionary attack, or with an unsuitable dictionary list.
TO BE CONTINUE
_____________________________________________________________________
Okay, so I'm not going to back track (forgive the pun) through the previous tutorial. If you aren't certain how to get to where I'm beginning this tutorial at, scroll down and read hacking WEP. It will fill you in on everything except putting your card into monitor mode and such.
So, first you will need to start up airodump-ng and capture packets from the AP. This time, however, do not add the --ivs, as you will want ALL the data in the packets. Look in the upper right corner of the window, just after the date and time. You will notice that the area is black and empty. This is where the four-way WPA handshake will show up when you have attained it. I will explain that in more detail later.
I will assume that you are now collecting packets in monitor mode. Packets by themselves are completely useless for cracking WPA. What we are interested in is the four-way handshake. To get this, we will use aireplay-ng to perform a deauth (de-authentication) attack, disconnecting the client from the AP, and forcing it to reconnect... also giving away the four-way handshake.
To do this, type in aireplay-ng -0 1 -a (AP MAC) -c (Client MAC) (your NIC)
Mine was aireplay-ng -0 1 -a 00:40:05:26:B3:C0 -c 00:16:CF:0B:0D:FD eth2

Now you should see a handshake appear in the window containing your running (you did leave it running, right?) airodump-ng program:

Now we need to get the key. Just as in the WEP cracking tutorial, I am going to make you do some of your own leg work. You will need to find a dictionary word list. You can also make your own, and add the pass phrase to the list. This screenshot shows an example of the list I made in a few seconds to show you the next steps:

Okay okay, you got me. This was done in Windows XP. I forgot to take a screenshot of the list in BackTrack 3b, and was too lazy to go back and do it again. You'll just have to pretend its all black and fancy and cool looking like the BackTrack GUI is.
Alright, so you have your dictionary list ready to run with aircrack-ng. Type in aircrack-ng -w (dictionary.lst/txt) -b (AP MAC) (dumpfile.cap)
Mine has aircrack-ng -w crack.txt -b 00:40:05:26:B3:C0 psk-02.cap

Now, if it finds the correct pass phrase in the dictionary list, you will be presented with the word:

Okay, so what did we learn here? Well, WPA-psk is more secure than WEP in that you must run a dictionary attack against it, and stronger passwords will require a rainbow table (don't worry, I may go into that in another blog). So it is theoretically more secure than WEP.
However, the pass phrase is only as secure as you make it. In this case, I set mine up to be very simple to facilitate this demonstration. However, using real words greatly diminishes the effectiveness of WPA, and it is highly suggested that you use special characters, upper case, lower case, and numbers in your passwords.
The second weakness in WPA-psk, is the reliance on the four-way handshake, in which the key is transmitted. It takes only a moment to run a deauth attack to force a handshake and grab the key.
Finally, WPA has the advantage of requiring a client to be connected before an attempt to crack can occur. Where WEP can be coaxed into transmitting packets, and therefore give the attacker IVs, WPA cracking needs that handshake with the pass phrase before any further progress can be made.
So WPA is far from perfect, but it can foil someone who is unprepared to run a dictionary attack, or with an unsuitable dictionary list.
TO BE CONTINUE
Sunday, February 3, 2008
Creating a customized system restore disk
I was going to do another writeup on BackTrack, but I decided to do it on an often overlooked portion of network security: backup and restore.
It is inevitable that even your best defense will fail you, and the data center or workstations will need to be restored to their original state. Because attempting to do this with normal installation CDs would make a new career field, several methods have been devised for making streamlined install CDs and network installations.
I will not talk about restoring servers in this entry, but focus on workstations for smaller companies.
There are two main options for creating these restore CDs. The first is Bart, the second is nLite. After reviewing both of the programs (which are free and available for download), I decided to use nLite because of its greater simplicity. However, it will not allow me to 3rd party programs, only drivers, themes, service packs, and updates can be integrated. Bart also has the advantage of booting in live mode. However, nLite is much easier to setup and run, and requires no interaction from the user.
So, to start with, download all the drivers you want to install on your system. You will want the binaries if possible. If not, you will need to unpackage them. A program called Universal Extractor is good for doing this, but does not work with 100% of the drivers available.



Now you will need to download updates, either from Microsoft, or as a lump download from RyanMV. Put them into a folder as well.
After this, head to Microsoft and download service pack 2 for IT pros. This will allow you to install service pack 2 if your CD does not include it already. Also, you can download service pack 3 when it is ready.
After doing this, you will need to copy your windows XP cd to another folder. When it is completed, download and install nLite. Run it, and you will begin at this screen:

Its pretty straight forward. Next is this screen:

Here you must navigate to the file you copied your Windows XP cd to and load it.

This screen will allow you to import a previous session. Each session requires you to make a fresh copy of Windows XP. However, it will also allow you to modify previous ISO's without completely rebuilding them. Assuming you have no past sessions, simply click next.

Here is where you will choose what to streamline. For this exercise, I chose all of them:

And then selected service pack 2 for integration:

Be patient, it takes a little bit of time:

Once this is finished, navigate to the hot fixes and patches you wish to add to your installation:


Click next and you will be at the add drivers screen. Add the drivers you desire and click next.

After the drivers are finished integrating, you will need to select options you wish to keep. Don't worry, they won't remove any vital system options, they will only prevent you from removing a service that you wish to keep by accident. Think of this stage as a filter stage. You are asked what you wish to to do, and choices are narrowed down based on your more broad answers.

I have a webcam, needed DHCP functionality for networking, media center codecs, printers, windows activation (never turn this off unless you have a corporate edition disk) and I like to run automatic updates.

This is the important part. You can remove programs and drivers from being installed on your system. There is a plethora of features which the average user or office worker does not need. Everything from games, to messenger, down to different languages and ancient drivers.

As you can see, there is something in almost every category that can be removed. Keep in mind that most drivers do not use the generic windows pre-load drivers, but their own proprietary applications.

Now the fun part. You can fully automate the disk by entering the product key and selecting a fully automated unattended mode. I turned off system restore because I back up my files on a different drive, and like keeping the extra space (2% of 160 gigs is still a lot).

For safety concerns, I disabled the default administrator account, and gave my own account those permissions. Brute force attacks are run against Administrator and Admin accounts most frequently. You can also add additional users if you require.

This area allows you to configure your network. If you have a domain controller, enter the domain name, user name, and password, as well as the organization. The computer name will have to be changed after installation if this is the case, however.

Because I preloaded my nVidia video card drivers, I set the screen resolution and refresh rate to the optimal setting. WARNING!!! If you exceed your monitor or video card's maximum refresh rate or resolution, you can damage them! If you aren't sure what the threshold is, leave them at default and change it later.

I strongly advise turning automatic updates on, include minor updates, and elevate non-admins if there are non-admin accounts.

When you are finished reviewing and selecting your options, click next and double check the options screen. This will allow you to tweak a few additional options, especially in the boot process.

This screen allows you to tweak your startup an registry options. There are a few things that basic users can do, such as adding an administrative tools menu to the start menu (its a feature I really like from Server 2003).

After clicking next, nLite will begin to construct the files it will use to generate the ISO. Be patient, this takes some time. There may be errors in your updates. nLite can usually work around them and generate the files regardless.

Success!!! The total installation was reduced by 172.4 megabytes, even though I added 45.67 megabytes of additional drivers. This is a very slim installation, and will lead to a less bloated registry and windows folder.

Now just generate the ISO image. Once this image is created, you can put a writable disk into the CD drive, and double click the ISO. It will then create your installation CD. You can also use other ISO recording applications as well.
Remember to BE CAUTIOUS with these CDs. Unlike a Bart CD that installs from a server on the domain, these CDs can be swiped and used on any other computers. This is not good if you have a corporate license. I would advise that you make only a limited number of copies, secure the ISO file, and regulate the distribution of the CDs.
I will try to post a writeup using Bart CDs, though I cannot promise it will be using a domain for remote installation.
It is inevitable that even your best defense will fail you, and the data center or workstations will need to be restored to their original state. Because attempting to do this with normal installation CDs would make a new career field, several methods have been devised for making streamlined install CDs and network installations.
I will not talk about restoring servers in this entry, but focus on workstations for smaller companies.
There are two main options for creating these restore CDs. The first is Bart, the second is nLite. After reviewing both of the programs (which are free and available for download), I decided to use nLite because of its greater simplicity. However, it will not allow me to 3rd party programs, only drivers, themes, service packs, and updates can be integrated. Bart also has the advantage of booting in live mode. However, nLite is much easier to setup and run, and requires no interaction from the user.
So, to start with, download all the drivers you want to install on your system. You will want the binaries if possible. If not, you will need to unpackage them. A program called Universal Extractor is good for doing this, but does not work with 100% of the drivers available.



Now you will need to download updates, either from Microsoft, or as a lump download from RyanMV. Put them into a folder as well.
After this, head to Microsoft and download service pack 2 for IT pros. This will allow you to install service pack 2 if your CD does not include it already. Also, you can download service pack 3 when it is ready.
After doing this, you will need to copy your windows XP cd to another folder. When it is completed, download and install nLite. Run it, and you will begin at this screen:

Its pretty straight forward. Next is this screen:

Here you must navigate to the file you copied your Windows XP cd to and load it.

This screen will allow you to import a previous session. Each session requires you to make a fresh copy of Windows XP. However, it will also allow you to modify previous ISO's without completely rebuilding them. Assuming you have no past sessions, simply click next.

Here is where you will choose what to streamline. For this exercise, I chose all of them:

And then selected service pack 2 for integration:

Be patient, it takes a little bit of time:

Once this is finished, navigate to the hot fixes and patches you wish to add to your installation:


Click next and you will be at the add drivers screen. Add the drivers you desire and click next.

After the drivers are finished integrating, you will need to select options you wish to keep. Don't worry, they won't remove any vital system options, they will only prevent you from removing a service that you wish to keep by accident. Think of this stage as a filter stage. You are asked what you wish to to do, and choices are narrowed down based on your more broad answers.

I have a webcam, needed DHCP functionality for networking, media center codecs, printers, windows activation (never turn this off unless you have a corporate edition disk) and I like to run automatic updates.

This is the important part. You can remove programs and drivers from being installed on your system. There is a plethora of features which the average user or office worker does not need. Everything from games, to messenger, down to different languages and ancient drivers.

As you can see, there is something in almost every category that can be removed. Keep in mind that most drivers do not use the generic windows pre-load drivers, but their own proprietary applications.

Now the fun part. You can fully automate the disk by entering the product key and selecting a fully automated unattended mode. I turned off system restore because I back up my files on a different drive, and like keeping the extra space (2% of 160 gigs is still a lot).

For safety concerns, I disabled the default administrator account, and gave my own account those permissions. Brute force attacks are run against Administrator and Admin accounts most frequently. You can also add additional users if you require.

This area allows you to configure your network. If you have a domain controller, enter the domain name, user name, and password, as well as the organization. The computer name will have to be changed after installation if this is the case, however.

Because I preloaded my nVidia video card drivers, I set the screen resolution and refresh rate to the optimal setting. WARNING!!! If you exceed your monitor or video card's maximum refresh rate or resolution, you can damage them! If you aren't sure what the threshold is, leave them at default and change it later.

I strongly advise turning automatic updates on, include minor updates, and elevate non-admins if there are non-admin accounts.

When you are finished reviewing and selecting your options, click next and double check the options screen. This will allow you to tweak a few additional options, especially in the boot process.

This screen allows you to tweak your startup an registry options. There are a few things that basic users can do, such as adding an administrative tools menu to the start menu (its a feature I really like from Server 2003).

After clicking next, nLite will begin to construct the files it will use to generate the ISO. Be patient, this takes some time. There may be errors in your updates. nLite can usually work around them and generate the files regardless.

Success!!! The total installation was reduced by 172.4 megabytes, even though I added 45.67 megabytes of additional drivers. This is a very slim installation, and will lead to a less bloated registry and windows folder.

Now just generate the ISO image. Once this image is created, you can put a writable disk into the CD drive, and double click the ISO. It will then create your installation CD. You can also use other ISO recording applications as well.
Remember to BE CAUTIOUS with these CDs. Unlike a Bart CD that installs from a server on the domain, these CDs can be swiped and used on any other computers. This is not good if you have a corporate license. I would advise that you make only a limited number of copies, secure the ISO file, and regulate the distribution of the CDs.
I will try to post a writeup using Bart CDs, though I cannot promise it will be using a domain for remote installation.
Friday, February 1, 2008
Ethical Implications of Hacking
This is not an entry that I am making from what I have learned from reading a book or browsing websites, but from interaction as a network infrastructure intern, computer technician hobbyist, and help desk employee. It is a bit of wisdom and musing that has been mixed together and coughed up into a paper. I think I would have rather done more work with BackTrack 3b, but I've run out of time this week. So do not look for any sources past my own personal experience on this matter.
As I learn and discover more in the ways of hacking, the greater I find the urge to try what I have learned on systems other than my own. Then I remind myself that it is no less than looking through someone's window. Is it morally right to stand outside a stranger's house and watch them through a window? Of course not, so why would it be any different to do it through a computer?
I believe the anonymity of hacking is what emboldens people, makes them feel empowered and just in their ability to gain access to personal documents, even if they do no harm. Yet this invasive behavior could only breed distrust and anger on any other level.
But the subjects of ethics is not relegated to adults. Is it ethical to teach someone young, perhaps in junior high, to hack computer systems? It is certainly possible for younger generations to learn at an early age, even as young as grade school. However, knowing and understanding are two very different principles. While script kiddies are dangerous, a full, bona fide hacker of that age still has no understanding of the harm they can cause, yet has more power to infiltrate private systems.
Without a firm grasp of ethics or understanding, the juvenile will then cause damage to the system, the result of which could cost millions. At the same time, however, an early exposure to such knowledge could give the child a head start on a lucrative career path. And the earlier they begin, the more potential they will have in the field of information security.
Perhaps, then, the ethical thing would not be to expose or deny, but to regulate access and activities involving this knowledge. Ultimately, the outcome of a child's life is dependent on their parents or guardians.
There is also a code of ethics for the workplace. Even for those not in a network security position, or even in the IT department. Having similar skills and knowledge does not give them a right to employ it. It may be that the services are required from time to time, or not at all. But services are limited to what an administrator would ask of the employee.
Using such skills because another employee needs access to restricted files, forgot their password, or wants to delete an email containing questionable material that they accidentally sent to the boss, is unethical. All networks are privately owned, and even administrators must practice self restraint.
And why should such care be taken if nobody will know? Indeed they may not know of that offense. However, all members of the Information Technology department make other employees nervous. We are often viewed as key holders, overseers, and judges. I have seen for myself the widespread belief that we have access to all information, records on all the employees, and know their computing habits by heart.
To become what people believe will enforce the notion that we are a body to be resisted, a department that spends the day finding reasons to fire or reprimand, and reduce the freedoms of other employees. To prevent this, it is the duty of all, in IT or not, who possess such skills to hack, to keep to the code of ethics and refrain from activities that would tarnish or reduce employee's faith in IT.
And those who live under the strongest code of ethics, the penetration testers and security administrators, must hold even closer to the code of ethics. Security administrators cannot break the code of ethics for the top level of management within a company. Likewise, penetration testers must attempt to access information that could be crippling to individuals or the company to ensure its safety. They are entrusted with many company secrets, and to release any vulnerabilities to the company instead of exploiting them for personal gain.
As I learn and discover more in the ways of hacking, the greater I find the urge to try what I have learned on systems other than my own. Then I remind myself that it is no less than looking through someone's window. Is it morally right to stand outside a stranger's house and watch them through a window? Of course not, so why would it be any different to do it through a computer?
I believe the anonymity of hacking is what emboldens people, makes them feel empowered and just in their ability to gain access to personal documents, even if they do no harm. Yet this invasive behavior could only breed distrust and anger on any other level.
But the subjects of ethics is not relegated to adults. Is it ethical to teach someone young, perhaps in junior high, to hack computer systems? It is certainly possible for younger generations to learn at an early age, even as young as grade school. However, knowing and understanding are two very different principles. While script kiddies are dangerous, a full, bona fide hacker of that age still has no understanding of the harm they can cause, yet has more power to infiltrate private systems.
Without a firm grasp of ethics or understanding, the juvenile will then cause damage to the system, the result of which could cost millions. At the same time, however, an early exposure to such knowledge could give the child a head start on a lucrative career path. And the earlier they begin, the more potential they will have in the field of information security.
Perhaps, then, the ethical thing would not be to expose or deny, but to regulate access and activities involving this knowledge. Ultimately, the outcome of a child's life is dependent on their parents or guardians.
There is also a code of ethics for the workplace. Even for those not in a network security position, or even in the IT department. Having similar skills and knowledge does not give them a right to employ it. It may be that the services are required from time to time, or not at all. But services are limited to what an administrator would ask of the employee.
Using such skills because another employee needs access to restricted files, forgot their password, or wants to delete an email containing questionable material that they accidentally sent to the boss, is unethical. All networks are privately owned, and even administrators must practice self restraint.
And why should such care be taken if nobody will know? Indeed they may not know of that offense. However, all members of the Information Technology department make other employees nervous. We are often viewed as key holders, overseers, and judges. I have seen for myself the widespread belief that we have access to all information, records on all the employees, and know their computing habits by heart.
To become what people believe will enforce the notion that we are a body to be resisted, a department that spends the day finding reasons to fire or reprimand, and reduce the freedoms of other employees. To prevent this, it is the duty of all, in IT or not, who possess such skills to hack, to keep to the code of ethics and refrain from activities that would tarnish or reduce employee's faith in IT.
And those who live under the strongest code of ethics, the penetration testers and security administrators, must hold even closer to the code of ethics. Security administrators cannot break the code of ethics for the top level of management within a company. Likewise, penetration testers must attempt to access information that could be crippling to individuals or the company to ensure its safety. They are entrusted with many company secrets, and to release any vulnerabilities to the company instead of exploiting them for personal gain.
Wednesday, January 23, 2008
New Methods of Hacking
This is where I will be talking about the new generation of hacking and theories.
Password Profiling
Okay, so everyone knows that the current brand of password cracking involves one of three different methods. One is a dictionary attack using real words from a dictionary list. Another is a brute force attack that systematically tries every possible number, letter, and character combination over a large amount of time. The third is to use a rainbow table.
What if there was an easier method to discover someone's password, that doesn't use random generation, but profiling? That is, a program that can scan a person's personal folders and files and look for patterns.
It looks as though the Wyd Password Profiler will do just that. By looking for patterns in the targets behavior or personality, the program is able to construct viable passwords.
As an example: Tom loves baseball. He has pictures of his favorite team, scores, screen savers, etc stored on his system. It is logical, therefore, that his password will contain something about this sports team, or one of the players. By knowing this information, the attacker can focus on that attack vector, instead of running a dictionary attack list that may only contain the word baseball (which would not be sufficient).
The purpose of this type of attack is not to build an extensive list to attack the victim with, but is instead used to take out false positives, and narrow down the possible passwords significantly.
Rogue Access Point Attack
Remember Microsoft Windows' ability to automatically connect you to your favorite networks? Well, that may not be the best feature Microsoft has thought up. By exploiting a bug in the wireless manager, an attacker can sniff out your favored networks, and change the SSID of their rogue network to match it. Windows will automatically connect you to that network, without alerting you. At this point, they are free to start scanning your computer, transmit malware, or or use a program like wireshark to capture your packets.
More information on this attack can be found here.
However, there is a potential defense against this, which uses the same program used to disconnect the victim from a good network (void11) and uses a matchlist that you generate to automatically refuse connections. However, it is limited to prism cards, and requires a bit of technical knowledge. You can find information on it here.
Password Profiling
Okay, so everyone knows that the current brand of password cracking involves one of three different methods. One is a dictionary attack using real words from a dictionary list. Another is a brute force attack that systematically tries every possible number, letter, and character combination over a large amount of time. The third is to use a rainbow table.
What if there was an easier method to discover someone's password, that doesn't use random generation, but profiling? That is, a program that can scan a person's personal folders and files and look for patterns.
It looks as though the Wyd Password Profiler will do just that. By looking for patterns in the targets behavior or personality, the program is able to construct viable passwords.
As an example: Tom loves baseball. He has pictures of his favorite team, scores, screen savers, etc stored on his system. It is logical, therefore, that his password will contain something about this sports team, or one of the players. By knowing this information, the attacker can focus on that attack vector, instead of running a dictionary attack list that may only contain the word baseball (which would not be sufficient).
The purpose of this type of attack is not to build an extensive list to attack the victim with, but is instead used to take out false positives, and narrow down the possible passwords significantly.
Rogue Access Point Attack
Remember Microsoft Windows' ability to automatically connect you to your favorite networks? Well, that may not be the best feature Microsoft has thought up. By exploiting a bug in the wireless manager, an attacker can sniff out your favored networks, and change the SSID of their rogue network to match it. Windows will automatically connect you to that network, without alerting you. At this point, they are free to start scanning your computer, transmit malware, or or use a program like wireshark to capture your packets.
More information on this attack can be found here.
However, there is a potential defense against this, which uses the same program used to disconnect the victim from a good network (void11) and uses a matchlist that you generate to automatically refuse connections. However, it is limited to prism cards, and requires a bit of technical knowledge. You can find information on it here.
BackTrack
DISCLAIMER: Yes, this will show you how to hack into a wireless network. This is very much ILLEGAL. The purpose of this writeup is for educational purposes only. I am demonstrating the weakness of WEP encryption on my own network. If you wish to try this for yourself, I suggest you buy a wireless router and attempt to crack that.
_____________________________________________________________________
I wanted to post a live instructional movie instead of a set of pictures. However, I am still attempting to get my wireless card working in a virtual environment and/or an open source video capturing utility that runs in Back Track 3.
I could list the set of programs I will be using here, but they are listed throughout the blog. I believe it is better to say that I am using Back Track 3 (beta) using a live install and a Linksys WMP11 wireless NIC. You can find details on downloading and installing Back Track 2 and 3 here.
Alright, there are a few things I'm leaving off the beginning. The first is setting your wireless card to monitor mode. I had a little trouble with this at first. I have to extend a thank you to Brian for pointing me in the right direction.
Another is the list of compatible wireless cards. You can find those circulating around the net (at the ubuntu website, the aircrack site, and a few others). I am also leaving off driver installation. Some wireless cards require madwifi drivers to work. You can find out more about this via the Madwifi webpage.
It is actually very easy to set your wireless NIC to monitor mode in Back Track 3. Play around with some of the programs, and if you are still having trouble, try the Remote Exploit Forums.
Okay, so you have your card in monitor mode (or you're just curious and want to read on). The first step is to make certain that your card is in fact running in monitor mode. To do this, open the terminal and type iwconfig Look for your wireless card. The window should be displaying as such:

Notice the second line in eth2? It says "Mode:Monitor." This confirms that the wireless card is set to monitor.
Now, you can do one of two things. The first is run a wireless sniffing program, that will allow you to see hidden SSID's. I will not be demonstrating that in this tutorial. Instead, we will use a program called airodump to capture the packets and create a file that we can use in a cracking program. There are several options you can set when using Airodump.

This may seem overwhelming at first, but its easy to figure out. The options we are interested in right now are: --ivs, -w, and -channel 6.
This is because I already know the target is using channel 6, and don't need to scan any other channels. --ivs will store only captured ivs. Ivs are initialization vectors that preamble the key. There are 16.7 million varieties, which may sound like a lot. However, they are only 3 bytes in size, and so even a weak computer can run an algorithm that checks for patterns and eventually breaks the wep key. For our purposes, we only need to record these. Finally, the -w or write option will write the stored information to a .cap file that we can use at a later time.
So we type in the command airodump-ng -w --ivs -channel 6 eth2
 \
\
Alright. Now airodump is running and pulling ivs out of packets. How long does this need to run for? It varies depending on the type of encryption and complexity of the code. In this case, it is a 64 bit hex code using WEP encryption. I'll let it run for 20 minutes, but I could probably do it in as few as 5 if I'm lucky.

Notice that there is a second wireless AP that popped up? Airodump will capture all available information on any selected channel, or even scan every channel within the range specified.
Now that the 20 minutes is up, we can press ctrl+c to stop the dump and exit back to the konsole. The -w command now creates a capture file with all the information we need.

We can see the name of the capture file is ivs-01.cap. Now, in the konsole, type aircrack-ng --help.
This brings up the aircrack options. Aircrack is the program we will use to crack the encryption and discover the code.

We really don't need any of the special options at this point. So simply type aircrack-ng ivs-01.cap. We are now presented with an option. Remember that other AP that came up when airodump was running? It saves all of this information in the file. If there were 10 ap's during the airodump process, there would be 10 ap's to choose from now. We are only interested in the first, which is airwave (the SSID of my router). So we type 1 and press enter.

Congradulations! There is the key to my wireless network. It took about .5 seconds to produce, though it is a very weak key with the worst possible encryption. I will look into cracking 128 bit WEP, and possibly WPA in the future.

_____________________________________________________________________
I wanted to post a live instructional movie instead of a set of pictures. However, I am still attempting to get my wireless card working in a virtual environment and/or an open source video capturing utility that runs in Back Track 3.
I could list the set of programs I will be using here, but they are listed throughout the blog. I believe it is better to say that I am using Back Track 3 (beta) using a live install and a Linksys WMP11 wireless NIC. You can find details on downloading and installing Back Track 2 and 3 here.
Alright, there are a few things I'm leaving off the beginning. The first is setting your wireless card to monitor mode. I had a little trouble with this at first. I have to extend a thank you to Brian for pointing me in the right direction.
Another is the list of compatible wireless cards. You can find those circulating around the net (at the ubuntu website, the aircrack site, and a few others). I am also leaving off driver installation. Some wireless cards require madwifi drivers to work. You can find out more about this via the Madwifi webpage.
It is actually very easy to set your wireless NIC to monitor mode in Back Track 3. Play around with some of the programs, and if you are still having trouble, try the Remote Exploit Forums.
Okay, so you have your card in monitor mode (or you're just curious and want to read on). The first step is to make certain that your card is in fact running in monitor mode. To do this, open the terminal and type iwconfig Look for your wireless card. The window should be displaying as such:

Notice the second line in eth2? It says "Mode:Monitor." This confirms that the wireless card is set to monitor.
Now, you can do one of two things. The first is run a wireless sniffing program, that will allow you to see hidden SSID's. I will not be demonstrating that in this tutorial. Instead, we will use a program called airodump to capture the packets and create a file that we can use in a cracking program. There are several options you can set when using Airodump.

This may seem overwhelming at first, but its easy to figure out. The options we are interested in right now are: --ivs, -w, and -channel 6.
This is because I already know the target is using channel 6, and don't need to scan any other channels. --ivs will store only captured ivs. Ivs are initialization vectors that preamble the key. There are 16.7 million varieties, which may sound like a lot. However, they are only 3 bytes in size, and so even a weak computer can run an algorithm that checks for patterns and eventually breaks the wep key. For our purposes, we only need to record these. Finally, the -w or write option will write the stored information to a .cap file that we can use at a later time.
So we type in the command airodump-ng -w --ivs -channel 6 eth2
 \
\Alright. Now airodump is running and pulling ivs out of packets. How long does this need to run for? It varies depending on the type of encryption and complexity of the code. In this case, it is a 64 bit hex code using WEP encryption. I'll let it run for 20 minutes, but I could probably do it in as few as 5 if I'm lucky.

Notice that there is a second wireless AP that popped up? Airodump will capture all available information on any selected channel, or even scan every channel within the range specified.
Now that the 20 minutes is up, we can press ctrl+c to stop the dump and exit back to the konsole. The -w command now creates a capture file with all the information we need.

We can see the name of the capture file is ivs-01.cap. Now, in the konsole, type aircrack-ng --help.
This brings up the aircrack options. Aircrack is the program we will use to crack the encryption and discover the code.

We really don't need any of the special options at this point. So simply type aircrack-ng ivs-01.cap. We are now presented with an option. Remember that other AP that came up when airodump was running? It saves all of this information in the file. If there were 10 ap's during the airodump process, there would be 10 ap's to choose from now. We are only interested in the first, which is airwave (the SSID of my router). So we type 1 and press enter.

Congradulations! There is the key to my wireless network. It took about .5 seconds to produce, though it is a very weak key with the worst possible encryption. I will look into cracking 128 bit WEP, and possibly WPA in the future.

Friday, January 18, 2008
Watching a hack attempt from the other side
Alright, I'm going to bounce back to hacking for a moment. I currently run an FTP server for friends and classwork. I am using filezilla, an opensource FTP server program available from http://filezilla-project.org/.
After installing a new router, I had let it sit idle. I recently wished to share some pictures with a friend, and so I opened the ports. As soon as I did so, someone started using a dictionary attack against it.

So I contemplated a few things. I needed to keep my server available, of course, but these attacks would eat up system resources, and though my passwords are secure, its impossible to say what the complexity of their program is.
I already have a timeout scheme set (5 seconds between failed attempts) but I decided to go one step further. I implemented a ban system. After 10 failed attempts in a single hour, they would be banned for an hour.
I could also have instituted an permanent ban. However, this would hamper availability too much. People forget their passwords.
So the result looks like this:

I also have some important information in the log files. One is the time of the attacks, the other is the IP address of the attacker. Notice that, despite there are multiple IPs, they are all in the same block. First, I wanted to know exactly where the attacks were originating. To do this, I used a simple website called the Community Geotarget IP Project. I entered the attacker's IP address into the whois, and was able to discover the country of origin, but little else:

So, I have the country of origin, Thailand, but I want to know more. So I decided to visit another IPWHOIS site. This one is DNS Stuff. A quick IP search was much more revealing:

This has revealed that the IP is owned by the Ministry of Education. It has contact information, probably for a network administrator and the head of the Ministry of Education.
At this point, its up to my discretion whether I wish to notify the Network Administrator, or go on about my business. If this was a major network, I would need to employ a large staff just to handle these situations, and so I would not pursue any action unless the attack was successful.
Let me step back for a moment and speak of the security implications.
As previously stated, my FTP server had been online, but the port was blocked, so nobody could actually "see" my server.
Two days ago, I opened the ports so that a friend could download from the server. In those two days, I counted at least 5 attacks. I can't be sure of exactly how many yet, because I have not checked the recorded log, only the displayed log:

How could so many attacks start from such remote places without any knowledge that my server even exists? Well, my first assumption is a port scanner. That is, a program that scans IP's, and checks to see if it gets any response from specific ports. In this case, it would scan for port 21, which is reserved for FTP programs. I decided to do a google search and see if I could turn up a program that does this.
My very first search turned up this.
So the software is very easy to find and install, and is not complicated to use. We can safely assume that the attacker is using this method to find my server. And if the process is that simple, how can I step up my security? I will be researching methods for this. However, I believe that if I push integrity too hard, I will lose too much availability.
Log File
Okay, so I've gone back and reviewed my log files. The main log file is over 8 megabytes now of pure, single line text. I pulled some of the IP's, but this is not nearly a comprehensive list:
217.204.34.34
75.94.180.204
202.143.182.204
80.229.40.186
134.39.100.71
222.211.79.106
209.252.98.185
222.200.161.12
61.135.142.220
86.105.40.246
61.129.52.230
This is about 20% of the total IP's that are in the log file. Each one has at least 30 failed attempts to brute force past the login prompt.
From this I've learned a couple things.
1. Log files suck. It's not too much fun to dig through thousands of log entries to find information, and further more, most of the information is rather useless. Do I need to know that I was attacked, unsuccessfully, 50 times by the same IP? Probably. But do I need a new log entry for each attack by the same IP address? No, I don't. Not in this format, anyway. A program that sorts and organizes this information using drop down menus or some such would be very nice.
2. Security is pretty important. If I had an administrator account with a weak password, all the information on the FTP server would be compromised.
3. Trying to balance Availability, Integrity, and Confidentiality is more difficult than it seems.
I am looking into a new hosting format that functions like FTP, but uses a web interface and works on port 80 instead of 21. This will increase availability, while hopefully increasing security as well. Port sniffing for port 80 is a pretty big waste of time. The program can be found at the HFS website.
I will post another blog when I have more information, or have decided on a course of action for the server.
After installing a new router, I had let it sit idle. I recently wished to share some pictures with a friend, and so I opened the ports. As soon as I did so, someone started using a dictionary attack against it.

So I contemplated a few things. I needed to keep my server available, of course, but these attacks would eat up system resources, and though my passwords are secure, its impossible to say what the complexity of their program is.
I already have a timeout scheme set (5 seconds between failed attempts) but I decided to go one step further. I implemented a ban system. After 10 failed attempts in a single hour, they would be banned for an hour.
I could also have instituted an permanent ban. However, this would hamper availability too much. People forget their passwords.
So the result looks like this:

I also have some important information in the log files. One is the time of the attacks, the other is the IP address of the attacker. Notice that, despite there are multiple IPs, they are all in the same block. First, I wanted to know exactly where the attacks were originating. To do this, I used a simple website called the Community Geotarget IP Project. I entered the attacker's IP address into the whois, and was able to discover the country of origin, but little else:

So, I have the country of origin, Thailand, but I want to know more. So I decided to visit another IPWHOIS site. This one is DNS Stuff. A quick IP search was much more revealing:

This has revealed that the IP is owned by the Ministry of Education. It has contact information, probably for a network administrator and the head of the Ministry of Education.
At this point, its up to my discretion whether I wish to notify the Network Administrator, or go on about my business. If this was a major network, I would need to employ a large staff just to handle these situations, and so I would not pursue any action unless the attack was successful.
Let me step back for a moment and speak of the security implications.
As previously stated, my FTP server had been online, but the port was blocked, so nobody could actually "see" my server.
Two days ago, I opened the ports so that a friend could download from the server. In those two days, I counted at least 5 attacks. I can't be sure of exactly how many yet, because I have not checked the recorded log, only the displayed log:

How could so many attacks start from such remote places without any knowledge that my server even exists? Well, my first assumption is a port scanner. That is, a program that scans IP's, and checks to see if it gets any response from specific ports. In this case, it would scan for port 21, which is reserved for FTP programs. I decided to do a google search and see if I could turn up a program that does this.
My very first search turned up this.
So the software is very easy to find and install, and is not complicated to use. We can safely assume that the attacker is using this method to find my server. And if the process is that simple, how can I step up my security? I will be researching methods for this. However, I believe that if I push integrity too hard, I will lose too much availability.
Log File
Okay, so I've gone back and reviewed my log files. The main log file is over 8 megabytes now of pure, single line text. I pulled some of the IP's, but this is not nearly a comprehensive list:
217.204.34.34
75.94.180.204
202.143.182.204
80.229.40.186
134.39.100.71
222.211.79.106
209.252.98.185
222.200.161.12
61.135.142.220
86.105.40.246
61.129.52.230
This is about 20% of the total IP's that are in the log file. Each one has at least 30 failed attempts to brute force past the login prompt.
From this I've learned a couple things.
1. Log files suck. It's not too much fun to dig through thousands of log entries to find information, and further more, most of the information is rather useless. Do I need to know that I was attacked, unsuccessfully, 50 times by the same IP? Probably. But do I need a new log entry for each attack by the same IP address? No, I don't. Not in this format, anyway. A program that sorts and organizes this information using drop down menus or some such would be very nice.
2. Security is pretty important. If I had an administrator account with a weak password, all the information on the FTP server would be compromised.
3. Trying to balance Availability, Integrity, and Confidentiality is more difficult than it seems.
I am looking into a new hosting format that functions like FTP, but uses a web interface and works on port 80 instead of 21. This will increase availability, while hopefully increasing security as well. Port sniffing for port 80 is a pretty big waste of time. The program can be found at the HFS website.
I will post another blog when I have more information, or have decided on a course of action for the server.
Sunday, January 13, 2008
Hacking x2
Now that I've established a little information on hacking and hackers, I'll update with some information that shows the procedures of hacking, and the dangers of being hacked. Once again, I will use publicly available material as references.
Injections
Not the kind that that was developed to rip off your insurance company, but the type that alters database and scripting code to allow admittance to otherwise locked sites. This is one of the more simple hacks, and requires surprisingly little skill. It does require that the target system lack necessary security and sanitation code. However, because many admins and webhosts are rather lazy, these hacks have remained useful for quite some time.
SQL Injection
A SQL (pronounced "sequel") Injection relies on the very basic database programming msSQL or mySQL to implement. Note that SQL is not the only language used for databases, but is quite common. It uses plain English (or country of choice) commands, such as "Select fieldlist from table ... etc etc"
These commands are entered from exposed fields on the internet. If you have ever seen a page that asks for your user name and password, for example, you are possibly looking at a SQL form. When you enter your user name and password, the database compares it to a field of user names, and then the password associated with the typed user name. If they match, you are allowed access. If not, you are given an error message.
Think of it as an excel spreadsheet. Each row corresponds to a certain type of data. So row one might be your user name, row two your password, and row three your email. When you type your user name, it finds that unique user name, and then checks to see if the password you entered is the same. If it returns true, you are allowed access.
Because SQL cannot interpret by itself if a benign user name and password was entered, or if another, malicious SQL command was given, it simply carries out the orders as it was designed to.
So an attacker will first begin by establishing these things:
1. Is this a SQL Database? If yes, skip to 2. If no, Skip to end
2. What is the field name for "username"
3. What is the field name for "password"
4. What is the field name for "email"
To establish if the target uses a SQL database, the attacker will feed it a short SQL snippet. Remember that a SQL database will understand any SQL commands, even if it can't run them or they produce an error. What is typed into the login field is not important, after all, passwords are used as the universal key, user names are merely a reference point. In the password field, a command such as x' or '1'='1 will be typed.
In any SQL database, when a comparison is called between two fields, if they match a value of true will be returned. Because "or" automatically interrupts the search, 1=1 is tacked onto the end of the resulting search. The password is most definately not "x" but before the database returns false, it reads the "or" statement and the subsequent "1=1." This statement, is of course, true. Because the database is looking for a true answer, not a false, it pushes the "true" value.
Now, you might think it silly to have the database "look" for a true answer instead of being stoic and neutral. However, you must think about a query in conventional terms. Say you are going to the grocery store to buy a gallon of milk. When you ask a sales clerk where the milk is, you do not say "where is the milk not?" He would have to take you to every part of the store the milk is not at before you could determine where the milk is. Instead, you ask "where is the milk?" Now he will take you to the precise location the milk is kept. Keep in mind that there is not a single jug with "milk" stenciled into it, but all forms of milk. He cannot tell you where the 2% milk is unless you ask him specifically.
The initial discovery of the milk would result in a return of "true." You can, of course, refine your search if possible, but the point remains.
Now, using this analogy, imagine you went into Sears and said "Where is the milk or drills?" The clerk would tell you that there is no milk, but he will not then tell you to go away. The "or" statement will inspire him to take you to the drills. There was no milk, but the query for drills returned true.
So, if the attacker initiates an injection such as x' or '1'='1, the database must respond. To do this, the attacker can use the "mail me my password" feature. Though there are other ways to do this, it must be a method that will return some sort of value. Remember that the attacker will be unable to see the actually SQL code.
Let us say that the return was "We have sent you an email with your password in it." This will tell the attacker that they have found a SQL database, and what's more, it is not "sanitized." That is, there is nothing checking the code before it is executed to ensure that an attack is not occurring. Keep in mind that this is executing code in the database, so someone was just sent an email with steps to recover their password. Just as no systems can keep hackers out, no hackers can crack undetected. There is always a log, some trace to tell they were or are working.
Okay, so the attacker knows this is a SQL database with little or no security. Now they need to build an image of what the database looks like in their mind. Though it is better to use a pen and paper or open a text document. Each field has a unique name. The password list, for example, may be password, passwrd, pword, secret, etc. Each field that must be exploited by the attack must be named. There is no easy way to do this, but almost all databases use the same basic words to denote the field. This is again attributed to the laziness of the designers or admins.
To begin this, the attacker will change the code slightly. Now it will look more like x' AND password IS NULL; --
AND is substituted for OR, because we don't want it to return true. This is especially true when working with the email field. The attacker doesn't want 10 change of password emails going out to all 10,000 people in the database. If an error such as "missing syntax" is returned, its the wrong field name. However, if the attacker gets a response such as "no match found" then they know it is the correct field name. The three most important fields for the attacker to acquire are "logon/user name, password, and email. Other fields can be found this way, but they really serve no purpose. Once the attacker has access to all the resources by hacking into the system, they can acquire the same information in a fraction of the time.
Now that the attacker has figured out the correct field names, they are ready to move on to gaining full access. To do this, they must either guess a password, or use a much easier method of overriding an existing user and changing their password with a SQL injection.
Note that the attacker may have access to one SQL database, but it may not be the database that stores login credentials. To verify this, first the table name must be acquired. The code for this is x' AND 1=(SELECT COUNT(*) FROM tabname); --. Note that the attacker must guess the table's name, however, as usual the names are generally obvious. Members, users, etc. The command x' AND tabname.email IS NULL; -- wil l verify that this is in fact the table that is being actively used for login credentials.
After all this is settled, the attacker will need a valid login. Remember that this information is readily available. Many sites set the user name to match the account name. On a forum, for example, the name you login with is the name that is displayed when you post in threads. Also some variation will be used for the real name of the webmaster or contact listed on the website.
Using that user name and the command:
x';
UPDATE listname
SET email = 'victim's@email.com'
WHERE email = 'youremail@email.com
The attacker injects the command to change the table, deleting the original email and substituting it with theirs.
Now the attacker simply initiates the "reset my password" function, and it sends the password reset link to their email.
They now have full administrator privileges to the system, or the credentials of another user which they can cause havoc with. At their victim's expense, of course.
A written source for this can be found here
Here are some video's of the attacks in action:
So...
Consider this a warning! Don't be lazy. Nobody can guess a password field named "Iowatachata" ... okay, so you aren't likely to tell your boss that you changed all the SQL fields to random sesame street characters. You can, however, sanitize the input so that only characters which are allowed for passwords can be entered into the database. The characters =, ;, and ' should never be valid characters for passwords or user names. Ensure that they will be rejected.
There are many more steps to securing a SQL database. However, as with all security operations, the methods of securing a system is far harder than the methods used to break the security.
Injections
Not the kind that that was developed to rip off your insurance company, but the type that alters database and scripting code to allow admittance to otherwise locked sites. This is one of the more simple hacks, and requires surprisingly little skill. It does require that the target system lack necessary security and sanitation code. However, because many admins and webhosts are rather lazy, these hacks have remained useful for quite some time.
SQL Injection
A SQL (pronounced "sequel") Injection relies on the very basic database programming msSQL or mySQL to implement. Note that SQL is not the only language used for databases, but is quite common. It uses plain English (or country of choice) commands, such as "Select fieldlist from table ... etc etc"
These commands are entered from exposed fields on the internet. If you have ever seen a page that asks for your user name and password, for example, you are possibly looking at a SQL form. When you enter your user name and password, the database compares it to a field of user names, and then the password associated with the typed user name. If they match, you are allowed access. If not, you are given an error message.
Think of it as an excel spreadsheet. Each row corresponds to a certain type of data. So row one might be your user name, row two your password, and row three your email. When you type your user name, it finds that unique user name, and then checks to see if the password you entered is the same. If it returns true, you are allowed access.
Because SQL cannot interpret by itself if a benign user name and password was entered, or if another, malicious SQL command was given, it simply carries out the orders as it was designed to.
So an attacker will first begin by establishing these things:
1. Is this a SQL Database? If yes, skip to 2. If no, Skip to end
2. What is the field name for "username"
3. What is the field name for "password"
4. What is the field name for "email"
To establish if the target uses a SQL database, the attacker will feed it a short SQL snippet. Remember that a SQL database will understand any SQL commands, even if it can't run them or they produce an error. What is typed into the login field is not important, after all, passwords are used as the universal key, user names are merely a reference point. In the password field, a command such as x' or '1'='1 will be typed.
In any SQL database, when a comparison is called between two fields, if they match a value of true will be returned. Because "or" automatically interrupts the search, 1=1 is tacked onto the end of the resulting search. The password is most definately not "x" but before the database returns false, it reads the "or" statement and the subsequent "1=1." This statement, is of course, true. Because the database is looking for a true answer, not a false, it pushes the "true" value.
Now, you might think it silly to have the database "look" for a true answer instead of being stoic and neutral. However, you must think about a query in conventional terms. Say you are going to the grocery store to buy a gallon of milk. When you ask a sales clerk where the milk is, you do not say "where is the milk not?" He would have to take you to every part of the store the milk is not at before you could determine where the milk is. Instead, you ask "where is the milk?" Now he will take you to the precise location the milk is kept. Keep in mind that there is not a single jug with "milk" stenciled into it, but all forms of milk. He cannot tell you where the 2% milk is unless you ask him specifically.
The initial discovery of the milk would result in a return of "true." You can, of course, refine your search if possible, but the point remains.
Now, using this analogy, imagine you went into Sears and said "Where is the milk or drills?" The clerk would tell you that there is no milk, but he will not then tell you to go away. The "or" statement will inspire him to take you to the drills. There was no milk, but the query for drills returned true.
So, if the attacker initiates an injection such as x' or '1'='1, the database must respond. To do this, the attacker can use the "mail me my password" feature. Though there are other ways to do this, it must be a method that will return some sort of value. Remember that the attacker will be unable to see the actually SQL code.
Let us say that the return was "We have sent you an email with your password in it." This will tell the attacker that they have found a SQL database, and what's more, it is not "sanitized." That is, there is nothing checking the code before it is executed to ensure that an attack is not occurring. Keep in mind that this is executing code in the database, so someone was just sent an email with steps to recover their password. Just as no systems can keep hackers out, no hackers can crack undetected. There is always a log, some trace to tell they were or are working.
Okay, so the attacker knows this is a SQL database with little or no security. Now they need to build an image of what the database looks like in their mind. Though it is better to use a pen and paper or open a text document. Each field has a unique name. The password list, for example, may be password, passwrd, pword, secret, etc. Each field that must be exploited by the attack must be named. There is no easy way to do this, but almost all databases use the same basic words to denote the field. This is again attributed to the laziness of the designers or admins.
To begin this, the attacker will change the code slightly. Now it will look more like x' AND password IS NULL; --
AND is substituted for OR, because we don't want it to return true. This is especially true when working with the email field. The attacker doesn't want 10 change of password emails going out to all 10,000 people in the database. If an error such as "missing syntax" is returned, its the wrong field name. However, if the attacker gets a response such as "no match found" then they know it is the correct field name. The three most important fields for the attacker to acquire are "logon/user name, password, and email. Other fields can be found this way, but they really serve no purpose. Once the attacker has access to all the resources by hacking into the system, they can acquire the same information in a fraction of the time.
Now that the attacker has figured out the correct field names, they are ready to move on to gaining full access. To do this, they must either guess a password, or use a much easier method of overriding an existing user and changing their password with a SQL injection.
Note that the attacker may have access to one SQL database, but it may not be the database that stores login credentials. To verify this, first the table name must be acquired. The code for this is x' AND 1=(SELECT COUNT(*) FROM tabname); --. Note that the attacker must guess the table's name, however, as usual the names are generally obvious. Members, users, etc. The command x' AND tabname.email IS NULL; -- wil l verify that this is in fact the table that is being actively used for login credentials.
After all this is settled, the attacker will need a valid login. Remember that this information is readily available. Many sites set the user name to match the account name. On a forum, for example, the name you login with is the name that is displayed when you post in threads. Also some variation will be used for the real name of the webmaster or contact listed on the website.
Using that user name and the command:
x';
UPDATE listname
SET email = 'victim's@email.com'
WHERE email = 'youremail@email.com
The attacker injects the command to change the table, deleting the original email and substituting it with theirs.
Now the attacker simply initiates the "reset my password" function, and it sends the password reset link to their email.
They now have full administrator privileges to the system, or the credentials of another user which they can cause havoc with. At their victim's expense, of course.
A written source for this can be found here
Here are some video's of the attacks in action:
So...
Consider this a warning! Don't be lazy. Nobody can guess a password field named "Iowatachata" ... okay, so you aren't likely to tell your boss that you changed all the SQL fields to random sesame street characters. You can, however, sanitize the input so that only characters which are allowed for passwords can be entered into the database. The characters =, ;, and ' should never be valid characters for passwords or user names. Ensure that they will be rejected.
There are many more steps to securing a SQL database. However, as with all security operations, the methods of securing a system is far harder than the methods used to break the security.
Thursday, January 10, 2008
HACKING
What is hacking?
Hacking is a widely feared and completely misconstrued activity. To the average person, a hacker is a kid with a super powerful computer in a clean room with super colorful display of pictures and characters flashing on the screen. They rapidly press random buttons and are suddenly presented with a prompt to enter basic commands.
The reality is, the definition of hacking is about as complex as the actual task.
First, there are multiple forms of hacking. The true "hacking" is usually done by college and graduate level students, or IT professionals probing for program or hardware weaknesses. White hat/red hat/black hat definitions are technically moot, since hacking for malicious purposes is covered by the term Cracking.
Using premade tools or walkthroughs is not hacking, and is considered being a "script kiddie." These are the younger (generally high school level) users who have little or no skill, but want to be considered "elite" by others. While the programs they use are capable of cracking into secured systems, the result is random damage and loss of data that the script kiddie has no facilities to understand.
Think of the difference in these examples:
Hackers: A group of painters are hired to paint a mural on the side of a building that others can see.
Crackers: Paint that same mural with the same skill, but do it without permission, leaving the owners of the building to hire someone to paint over it.
Script Kiddie: A kid with a can of spray paint who draws crude pictures of genitalia on street signs.
How does hacking work?
Hacking is essentially solving a complex puzzle involving a constantly evolving set of rules, math, and computer language. Some "hacks" as they are called, are actually quite simple, and are a result of the laziness of the software engineers, others require nothing short of a mathematical genius to solve.
If one is curious, they have only browse a video sharing site, such as youtube.
This is an example of a more complex bluetooth hack:
However, some are a bit more simple, and show the dangers of being hacked a little better. This is another bluetooth hack that is done much quicker using one cellphone to attack another. Note that most bluetooth has a range of approximately 10 meters, which is a little under 30 feet... the perfect distance for someone to hack from the other side of a starbucks. Some, more powerful bluetooth devices can transmit and recieve up to 100 meters:
However, some tutorials will even go in depth and show you the entire process of hacking:
This makes it pretty easy to start basic hacking. There are many more places that yield advanced information. Sources other than the internet also exist. For example, in high school, I visited my local radioshack, and found a large book with every radio frequency used by the DOD, DOT, EMS, and Air Traffic Control/FAA. These types of books also exist for IP's and security protocols in place for the same entities.
A quick google turned up this in reguard to DoD IPv4 allocation (click).
This is a publicly available list of IPv4 Class A assignments. Its a little like putting a bullseye on a tank. Everyone knows where to aim.
Do not be mistaken, however. Just because you know where your target is, doesn't necessarily mean hacking it will be easy.
Why bother?
Each individual has their own reasons, and this is why there are multiple names for "hackers." While a hacker may try to prove a system is vulnerable, or be curious about the contents of a server, they will leave the system in the same state they discovered it. They rarely ever harm a network, and if so, its usually an accident.
Crackers, on the other hand, use their skills to damage or destroy data, systems, and /or deny other users the ability to access network resources. Though money may be a secondary motive, their primary is simply destruction and bragging rights.
Emerging Threats
As computers and computing knowledge becomes more prevalent, the number of attackers and attacks continue to increase. The lure of easy money and soft targets of opportunity for a new breed of terrorist is too strong to ignore. Industrial espionage is becoming common place.
What Hacking is Not
Asking someone for their password, then using it, is not hacking. That is social engineering. This goes for looking over someone's shoulder or claiming to be the last prince of an African country named Robatswania. These attacks are made on those who are, sorry to say, ignorant or uninformed.
Identity theft is not hacking. The information may have come from hacking, but identity theft is not remotely exclusive to hacking. It is common for the information to be found in dumpsters, recycle bins, and laying right on somebody's desk. The forged documents can be created on a computer without any access to the internet.
What Hacking will not Accomplish
Hackers cannot make your computer explode and kill you.
Hackers cannot steal any information that is not stored electronically. If your filing cabinet is pried open when you come home, that is burglary, not cracking. They can't hijack all the tv stations in the world to broadcast a message.
It really comes down to information and electronic storage.
How to avoid being hacked
1. don't use a computer.
Thats pretty much it. Any information you send over a network passes many nodes and is stored in many forms in many locations. The potential for your system to be hacked or cracked exists while it is connecting to the internet, or any network or machine that is connected to the internet.
There are, of course, the standard methods of weeding out the weaker hackers, such as a firewall, anti-virus, security updates etc. The biggest defense that a common person has, is to remain anonymous. Few people will waste their time on a system with no information or value.
Hacking is a widely feared and completely misconstrued activity. To the average person, a hacker is a kid with a super powerful computer in a clean room with super colorful display of pictures and characters flashing on the screen. They rapidly press random buttons and are suddenly presented with a prompt to enter basic commands.
The reality is, the definition of hacking is about as complex as the actual task.
First, there are multiple forms of hacking. The true "hacking" is usually done by college and graduate level students, or IT professionals probing for program or hardware weaknesses. White hat/red hat/black hat definitions are technically moot, since hacking for malicious purposes is covered by the term Cracking.
Using premade tools or walkthroughs is not hacking, and is considered being a "script kiddie." These are the younger (generally high school level) users who have little or no skill, but want to be considered "elite" by others. While the programs they use are capable of cracking into secured systems, the result is random damage and loss of data that the script kiddie has no facilities to understand.
Think of the difference in these examples:
Hackers: A group of painters are hired to paint a mural on the side of a building that others can see.
Crackers: Paint that same mural with the same skill, but do it without permission, leaving the owners of the building to hire someone to paint over it.
Script Kiddie: A kid with a can of spray paint who draws crude pictures of genitalia on street signs.
How does hacking work?
Hacking is essentially solving a complex puzzle involving a constantly evolving set of rules, math, and computer language. Some "hacks" as they are called, are actually quite simple, and are a result of the laziness of the software engineers, others require nothing short of a mathematical genius to solve.
If one is curious, they have only browse a video sharing site, such as youtube.
This is an example of a more complex bluetooth hack:
However, some are a bit more simple, and show the dangers of being hacked a little better. This is another bluetooth hack that is done much quicker using one cellphone to attack another. Note that most bluetooth has a range of approximately 10 meters, which is a little under 30 feet... the perfect distance for someone to hack from the other side of a starbucks. Some, more powerful bluetooth devices can transmit and recieve up to 100 meters:
However, some tutorials will even go in depth and show you the entire process of hacking:
This makes it pretty easy to start basic hacking. There are many more places that yield advanced information. Sources other than the internet also exist. For example, in high school, I visited my local radioshack, and found a large book with every radio frequency used by the DOD, DOT, EMS, and Air Traffic Control/FAA. These types of books also exist for IP's and security protocols in place for the same entities.
A quick google turned up this in reguard to DoD IPv4 allocation (click).
This is a publicly available list of IPv4 Class A assignments. Its a little like putting a bullseye on a tank. Everyone knows where to aim.
Do not be mistaken, however. Just because you know where your target is, doesn't necessarily mean hacking it will be easy.
Why bother?
Each individual has their own reasons, and this is why there are multiple names for "hackers." While a hacker may try to prove a system is vulnerable, or be curious about the contents of a server, they will leave the system in the same state they discovered it. They rarely ever harm a network, and if so, its usually an accident.
Crackers, on the other hand, use their skills to damage or destroy data, systems, and /or deny other users the ability to access network resources. Though money may be a secondary motive, their primary is simply destruction and bragging rights.
Emerging Threats
As computers and computing knowledge becomes more prevalent, the number of attackers and attacks continue to increase. The lure of easy money and soft targets of opportunity for a new breed of terrorist is too strong to ignore. Industrial espionage is becoming common place.
What Hacking is Not
Asking someone for their password, then using it, is not hacking. That is social engineering. This goes for looking over someone's shoulder or claiming to be the last prince of an African country named Robatswania. These attacks are made on those who are, sorry to say, ignorant or uninformed.
Identity theft is not hacking. The information may have come from hacking, but identity theft is not remotely exclusive to hacking. It is common for the information to be found in dumpsters, recycle bins, and laying right on somebody's desk. The forged documents can be created on a computer without any access to the internet.
What Hacking will not Accomplish
Hackers cannot make your computer explode and kill you.
Hackers cannot steal any information that is not stored electronically. If your filing cabinet is pried open when you come home, that is burglary, not cracking. They can't hijack all the tv stations in the world to broadcast a message.
It really comes down to information and electronic storage.
How to avoid being hacked
1. don't use a computer.
Thats pretty much it. Any information you send over a network passes many nodes and is stored in many forms in many locations. The potential for your system to be hacked or cracked exists while it is connecting to the internet, or any network or machine that is connected to the internet.
There are, of course, the standard methods of weeding out the weaker hackers, such as a firewall, anti-virus, security updates etc. The biggest defense that a common person has, is to remain anonymous. Few people will waste their time on a system with no information or value.
Subscribe to:
Posts (Atom)