_____________________________________________________________________
Okay, so I'm not going to back track (forgive the pun) through the previous tutorial. If you aren't certain how to get to where I'm beginning this tutorial at, scroll down and read hacking WEP. It will fill you in on everything except putting your card into monitor mode and such.
So, first you will need to start up airodump-ng and capture packets from the AP. This time, however, do not add the --ivs, as you will want ALL the data in the packets. Look in the upper right corner of the window, just after the date and time. You will notice that the area is black and empty. This is where the four-way WPA handshake will show up when you have attained it. I will explain that in more detail later.
I will assume that you are now collecting packets in monitor mode. Packets by themselves are completely useless for cracking WPA. What we are interested in is the four-way handshake. To get this, we will use aireplay-ng to perform a deauth (de-authentication) attack, disconnecting the client from the AP, and forcing it to reconnect... also giving away the four-way handshake.
To do this, type in aireplay-ng -0 1 -a (AP MAC) -c (Client MAC) (your NIC)
Mine was aireplay-ng -0 1 -a 00:40:05:26:B3:C0 -c 00:16:CF:0B:0D:FD eth2
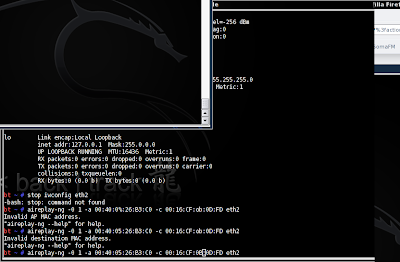
Now you should see a handshake appear in the window containing your running (you did leave it running, right?) airodump-ng program:
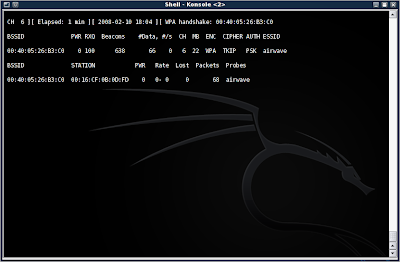
Now we need to get the key. Just as in the WEP cracking tutorial, I am going to make you do some of your own leg work. You will need to find a dictionary word list. You can also make your own, and add the pass phrase to the list. This screenshot shows an example of the list I made in a few seconds to show you the next steps:
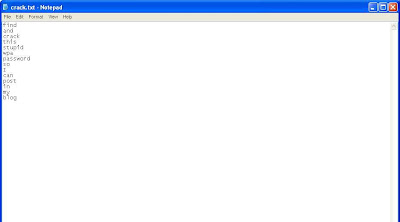
Okay okay, you got me. This was done in Windows XP. I forgot to take a screenshot of the list in BackTrack 3b, and was too lazy to go back and do it again. You'll just have to pretend its all black and fancy and cool looking like the BackTrack GUI is.
Alright, so you have your dictionary list ready to run with aircrack-ng. Type in aircrack-ng -w (dictionary.lst/txt) -b (AP MAC) (dumpfile.cap)
Mine has aircrack-ng -w crack.txt -b 00:40:05:26:B3:C0 psk-02.cap
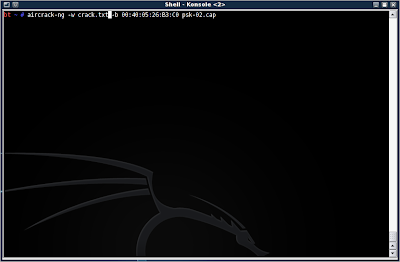
Now, if it finds the correct pass phrase in the dictionary list, you will be presented with the word:
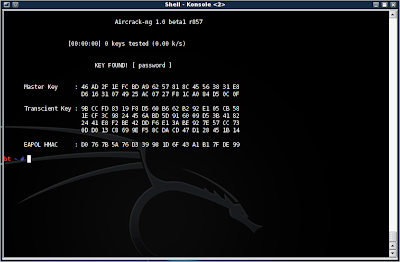
Okay, so what did we learn here? Well, WPA-psk is more secure than WEP in that you must run a dictionary attack against it, and stronger passwords will require a rainbow table (don't worry, I may go into that in another blog). So it is theoretically more secure than WEP.
However, the pass phrase is only as secure as you make it. In this case, I set mine up to be very simple to facilitate this demonstration. However, using real words greatly diminishes the effectiveness of WPA, and it is highly suggested that you use special characters, upper case, lower case, and numbers in your passwords.
The second weakness in WPA-psk, is the reliance on the four-way handshake, in which the key is transmitted. It takes only a moment to run a deauth attack to force a handshake and grab the key.
Finally, WPA has the advantage of requiring a client to be connected before an attempt to crack can occur. Where WEP can be coaxed into transmitting packets, and therefore give the attacker IVs, WPA cracking needs that handshake with the pass phrase before any further progress can be made.
So WPA is far from perfect, but it can foil someone who is unprepared to run a dictionary attack, or with an unsuitable dictionary list.
TO BE CONTINUE
No comments:
Post a Comment