Sunday, March 6, 2011
Absence
Sorry about the absence. I've just been through a motorcycle crash and had a few other personal things to attend. It never makes for punctual work, let me tell you. I'll be continuing the blog this Friday.
Friday, February 11, 2011
Hamachi Virtual Networks
Hey all and welcome to another exciting tutorial. In my last blog, I mentioned using ssh and Hamachi to keep your data safe, even when browsing the interwebs at your local hack- I mean coffee shop. Today, I'll be running you through configuring Hamachi to utilize your home network. In addition to providing a secure tunnel for browsing, Hamachi also allows you to transfer documents from your home computer/server, keep your work place connected, and allow for collaboration on projects with people around the world.
The first thing that you will need to do is download and install Hamchi. The installation process is very easy and straight forward, so I won't walk you through it.
Once Hamachi is installed and online, you will need to create a new network. Select Network> Create a new network.Create a meaningful name and highly secure password for your new network. Remember, if someone knows your network name, they can attempt to break in. The first line of security is obscurity:
After the network has been created, you will need to add computers. To do this, install Hamachi on any computer you want connected to the VPN. Select Network>Join Network:
Now you are free to set share permissions to files as you see fit. That is beyond the scope of this tutorial, however. Once you have configured network shares to your liking, you are free to move about in your local java joints and connect to the internet via your home network.
Note: You might need to configure your home router to pass port 80 to a computer running Hamachi. Not all routers explicitly require this, however.
The idea behind Hamachi is to allow for a secure tunnel through port 80, which will be available anywhere that the internet is. This includes your work place and libraries. Many other solutions use separate ports to function, and these are typically disabled to prevent other shenanigans.
Hamachi is free for up to 10 computers at a time (more than enough for the typical home user) and offers a secure means of staying connected on the go. Happy tunneling.
Labels:
file sharing,
free wifi,
Hamachi,
mobile security,
private tunnel,
Tunneling,
tutorial,
VPN
Friday, February 4, 2011
Firesheep
As if it wasn't enough that we had to worry about that seedy looking guy with quick fingers and shifty eyes at the local coffee shop, now we have to worry about 10 year olds too. Why you ask? Codebutler just released a firefox plugin that captures outbound cookies that are loaded with login credentials and session information. It's essentially a form of session hijacking, but with a simple point and click interface.
Yeah, it's that simple. So, what can you do to safeguard from these attacks? Honestly, there isn't much. It is the responsibility of the companies to enable SSL security instead of relying on unencrypted cookies.
Exactly how easy is it to use firesheep to hijack someone's facebook account? Well, you're about to find out. Here is a step by step guide that shows firesheep in action:
1) Download the latest release of Mozilla Firefox (if you haven't already). The version you need is 3.6.12 or higher.
2) Download and install the latest version of WinPCap.
Note: Both of these installs should require less than 15 minutes depending on your internet connection.
3) Download the Firesheep plug-in.
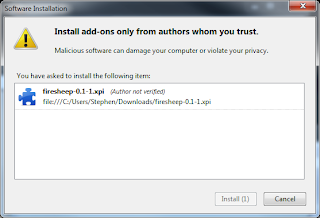
4) Install the plug-in by selecting Tools>Add-ons then dragging the downloaded plug-in to the add-on window:
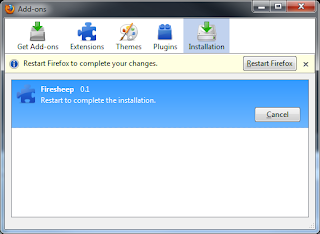
5) Click install after the countdown expires:

6) Click the button to restart Firefox:

7)Press ctrl + shift + S to open the firesheep sidebar:

8) Click on the small gear at the bottom of the side bar and select Preferences to open the configuration window. On the Interface drop down menu, make certain that your current network device is selected. If your wireless card isn't listed, then select Microsoft or whatever generic name appears:
9) Click the Start Capturing button:
10) Open an Internet Explorer, Chrome, Opera, or Safari window and browse your facebook account.
11) Watch the results appear in Firesheep:

Yeah, it's that simple. So, what can you do to safeguard from these attacks? Honestly, there isn't much. It is the responsibility of the companies to enable SSL security instead of relying on unencrypted cookies.
However, there are a couple things you can do to protect your data:
1) Use a VPN program such as Hamachi to securely tunnel the connection to your home network.
2) Use SSH to create a secure connection (not to be mistaken with SSL, which enables HTTPS).
Stay tuned for future updates that deal with Hamachi and SSH for added security and large scale firewall breaching.
Labels:
facebook,
firefox hacks,
firesheep,
gmail,
script kiddies,
social network hacking,
winpcap
Blog is now available at amazon.com
I'm going to reactivate this blog and continue with security guides and how-to's for average users. If you own a Kindle device, you can subscribe to this blog here. I will be posting a guide to firesheep later today.
Monday, March 17, 2008
State of the Media
This is more of an opinion blog than anything else. However, if I have noticed any trend during all the research I have done for this class, it is one of utter silence from the US Media. I have no fondness for media to begin with, but the complete lack of coverage for cyber attacks, theft, vandalism, and open hostilities is appalling. I would imagine that an attack on our government's nexus of military control would get a little more attention. And of widespread attacks on financial institutions? 30 second blip in the morning news.
Granted, some news agencies do have a section on information security, but I don't believe they are doing enough to make the public aware at just how vulnerable the country's financial and defense data is. I believe that more public knowledge would lead to outrage, not panic, and that congress would be forced to step up funding, and follow Bush's lead to strengthen our data and networks from cyber criminals.
Granted, some news agencies do have a section on information security, but I don't believe they are doing enough to make the public aware at just how vulnerable the country's financial and defense data is. I believe that more public knowledge would lead to outrage, not panic, and that congress would be forced to step up funding, and follow Bush's lead to strengthen our data and networks from cyber criminals.
IFRAME Attacks
A week ago, hackers began a scam to redirect people from hundreds of thousands of sites, to malware infected sites. These attacks began one week ago, and continue, expanding at a steady pace. The hackers are utilizing IFRAME injections, and have so far infected 401,000 pages. Experts believe that this is a staging point for a massive, widespread pharming attack. However, the attacks seem to be originating from the Russian Business Network. (source)
This is a perfect example of why Eastern Bloc countries are so dangerous. With most of the worlds malware and illegal sites being hosted in countries that are out of the reach of US and NATO law enforcement organizations, there is little we can do aside from blocking all web traffic that originates in that side of the world, and place a full scale embargo on them to make US credit card and bank numbers far less appealing.
Also, these unified attacks match the description of an act of war to the letter. It weakens our country's infrastructure, endangers the wellbeing of US citizens at home and abroad, and undermines US Military intelligence. I would not be surprised if these actions cause a full scale war in the future.
This is a perfect example of why Eastern Bloc countries are so dangerous. With most of the worlds malware and illegal sites being hosted in countries that are out of the reach of US and NATO law enforcement organizations, there is little we can do aside from blocking all web traffic that originates in that side of the world, and place a full scale embargo on them to make US credit card and bank numbers far less appealing.
Also, these unified attacks match the description of an act of war to the letter. It weakens our country's infrastructure, endangers the wellbeing of US citizens at home and abroad, and undermines US Military intelligence. I would not be surprised if these actions cause a full scale war in the future.
Monday, March 10, 2008
China waging cyber war?
This week, the US Military declared China a "cyber threat" and says they are continuing to wage war in cyberspace using a doctrine of "non-contact warfare." (Source is here). This comes after Germany's accusations in August that the Chinese military sponsored attacks against computers owned by Germany's top officials. In December, the UK's Mi5 warned corporations to be cautious of Chinese attacks.
These recent attacks have convinced the Bush administration to allocate $30 billion towards securing federal networks over the next five to seven years.
The world seems to be getting increasingly suspicious and edgy about China these days, and it is not surprising, considering their recent ability to knock satellites out of orbit. This capability, combined with information garnered from penetration of defense and intelligence networks, would give them unparalleled first strike capabilities.
Armies from developed nations in the west and Europe rely heavily on satellite communications and guidance system for munitions deployment, early detection and warning, and logistical commands. This is compounded by market and financial infrastructure that is entirely reliant on computer systems and networks with national and global communication.
Considering China's move to firewall their entire country and strictly regulate all information into and out of the country, they have much to do if they intend to ease the minds of the rest of the world.
These recent attacks have convinced the Bush administration to allocate $30 billion towards securing federal networks over the next five to seven years.
The world seems to be getting increasingly suspicious and edgy about China these days, and it is not surprising, considering their recent ability to knock satellites out of orbit. This capability, combined with information garnered from penetration of defense and intelligence networks, would give them unparalleled first strike capabilities.
Armies from developed nations in the west and Europe rely heavily on satellite communications and guidance system for munitions deployment, early detection and warning, and logistical commands. This is compounded by market and financial infrastructure that is entirely reliant on computer systems and networks with national and global communication.
Considering China's move to firewall their entire country and strictly regulate all information into and out of the country, they have much to do if they intend to ease the minds of the rest of the world.
Labels:
China,
global,
governments,
intelligence,
satellites,
space,
warfare
Subscribe to:
Posts (Atom)




