Exactly how easy is it to use firesheep to hijack someone's facebook account? Well, you're about to find out. Here is a step by step guide that shows firesheep in action:
1) Download the latest release of Mozilla Firefox (if you haven't already). The version you need is 3.6.12 or higher.
2) Download and install the latest version of WinPCap.
Note: Both of these installs should require less than 15 minutes depending on your internet connection.
3) Download the Firesheep plug-in.
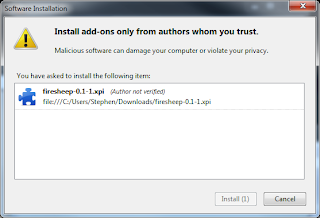
4) Install the plug-in by selecting Tools>Add-ons then dragging the downloaded plug-in to the add-on window:
5) Click install after the countdown expires:
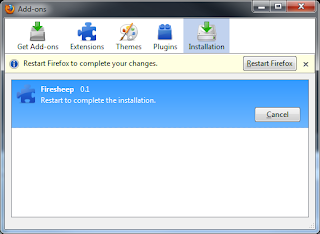
6) Click the button to restart Firefox:
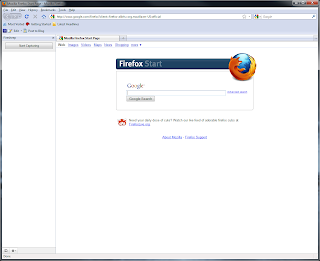
7)Press ctrl + shift + S to open the firesheep sidebar:
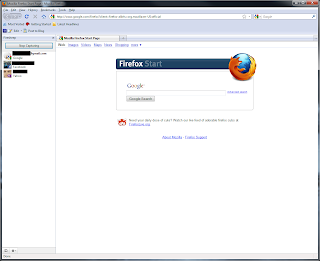
8) Click on the small gear at the bottom of the side bar and select Preferences to open the configuration window. On the Interface drop down menu, make certain that your current network device is selected. If your wireless card isn't listed, then select Microsoft or whatever generic name appears:
9) Click the Start Capturing button:
10) Open an Internet Explorer, Chrome, Opera, or Safari window and browse your facebook account.
11) Watch the results appear in Firesheep:
Yeah, it's that simple. So, what can you do to safeguard from these attacks? Honestly, there isn't much. It is the responsibility of the companies to enable SSL security instead of relying on unencrypted cookies.
However, there are a couple things you can do to protect your data:
1) Use a VPN program such as Hamachi to securely tunnel the connection to your home network.
2) Use SSH to create a secure connection (not to be mistaken with SSL, which enables HTTPS).
Stay tuned for future updates that deal with Hamachi and SSH for added security and large scale firewall breaching.



1 comment:
Should correct this to say that its effectively jacking your sessions. Since packets were not encrypted, it wasn't hard to rebuild the session data and spoof the victim's machine.
Post a Comment